- Site Collector Overview
- Get Started with Site Collectors
- Install Site Collector
- Set Up Collectors
- Sign Up for the Early Access Program: Site Collectors
- Choose the Right Collector based on Data Sources
- Set Up Archive Windows Collector
- Set Up Archive Linux Collector
- Set Up EStreamer Collector
- Set Up Fortinet Collector
- Set Up IBM Security QRadar Collector
- Set Up Kafka Collector
- Set Up Splunk Collector
- Set Up Linux File Collector
- Set Up Microsoft SQL Collector
- Set Up MySQL Collector
- Set Up Oracle Collector
- Set Up Syslog Collector
- Set Up Windows Active Directory Collector
- Set Up Windows Event Log Collector
- Set Up Windows File Collector
- Manage Site Collectors
- Apply Antivirus Exclusions
- Migrate to the New-Scale Site Collectors Service
- Modify Collector Configuration
- Modify a Site Collector Instance
- Manage Templates
- Monitor Log Sources
- Add Filters to Set Egress Log Filtering Conditions
- New Site Collector Management Service NGSCD
- Regenerate Certificates for Collectors
- Upgrade the Site Collector
- Upgrade the Site Collector Specifications
- Vulnerability Remediation Policy
- Site Collector Monitoring
- Troubleshoot the Site Collector
- Pre-checks failed during Site Collector installation and upgrade
- Site Collector UI shows the status INSTALLATION_ERROR
- Download Support Packages for Troubleshooting
- How to reboot the Virtual Machine (VM) successfully to apply security updates?
- What information must be added while creating a support ticket to resolve an issue?
- Site Collector UI is not displaying the heartbeats
- Splunk Collector can't be set up
- Splunk Collector is set up however, logs are not reaching DL/AA
- Only a few of the installed Splunk Collectors are processing logs or EPS has dropped by 50% as compared to last hour
- The Windows Active Directory Collector (formerly known as LDAP Collector) is set up, however, the context data is not reaching DL/AA
- The Windows Active Directory Collector (formerly known as LDAP Collector) is stuck in the ‘Update’ mode after deployment
- Installation is initiated; however, the collector shows the status as ‘Setting Up’ for some time
- Data Lake and Advanced Analytics Does Not Show Context Data
- Context Data from Windows Active Directory Collector is Segmented
- Minifi Permission Denied - Logback.xml File Missing and Config File Update - Failed Error Occurred while Installing the Windows Event Log Collector
- Where should I upload proxy certificates if I am running proxy with TLS interception?
- How to upgrade Linux collector instance?
Site Collector Overview
Site Collector provides a cloud-native data platform for ingesting data from on-premises log sources and active directories into the New-Scale Security Operations Platform with easy onboarding process, monitoring, and management through centralized cloud user interface.
Site Collector contains Site Collector core, Site Collector app, and Collectors to:
Streamline data onboarding by using common templates and use cases
Apply data compression before logs are uploaded to Exabeam cloud
Provide clarity for data processing and processed log volume reporting
Offer proactive monitoring and data altering
Site Collector Architecture
Site Collector collects messages, transfers, persists, and securely uploads event data; and connects to the New-Scale Security Operations Platform. Site Collector is the managed entry point for logs to be routed to other processing tools, such as Advanced Analytics, Data Lake, Incident Responder, and Case Manager in the Exabeam Security Management Platform. Site collectors gather logs from external servers, systems, and data centers.
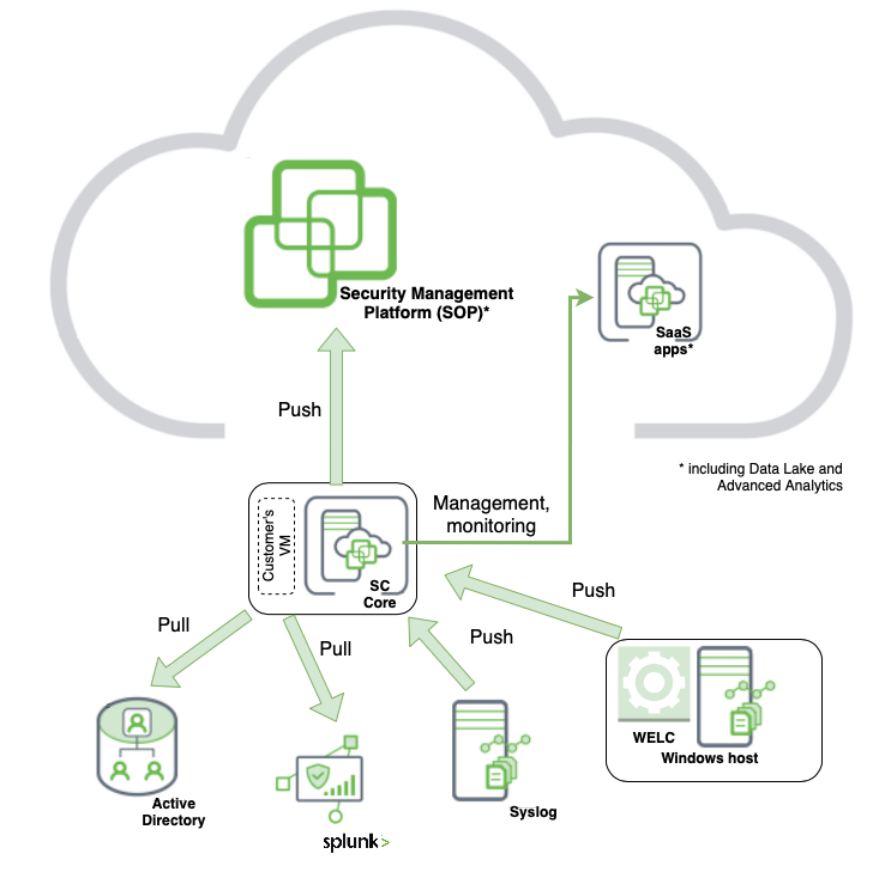
Component | Description |
|---|---|
Site Collector | Ingests data from on-premises log sources and on-premises active directory (AD) into Exabeam Cloud with a simple onboarding process, basic monitoring, and management over centralized cloud user interface (UI). |
Site Collector Core | Helps to:
|
Site Collector App | Enables end to end log collector setup, configuration, and monitoring. The application is integrated with Site Collector Core, and other Exabeam Cloud applications and products. |
Collector | Includes Site Collector flows, out-of-the-box processors and groups, custom processors, and other components and integrations developed for receiving logs or context from various sources, and sending the logs or context to the New-Scale Security Operations Platform. There are two types of collectors: agent collectors and server-side collectors.
NoteTo maintain optimal performance, the collector and Site Collector Core must always be running on their latest supported versions. Using an outdated version of collectors with a newer version of Site Collector Core may cause compatibility issues. Only the last three released versions of both collector and Site Collector Core are supported. In case of any issues, update the collector and Site Collector Core to their latest versions. If the error persists, contact Customer Support for further assistance. |
Windows Active Directory (formerly known as LDAP) Collector | Includes Site Collector flows, built-in processors, groups, custom processors, other components, and integrations aimed at pulling context data from your active directory (AD), and pushing the data to the New-Scale Security Operations Platform for contextual data processing. |
Splunk Collector | Pulls logs from your Splunk server and pushes the logs to the New-Scale Security Operations Platform. At collector level, a single Splunk collector instance can ingest 7k EPS events at 2.5KB average size. For enterprise specifications, you can simultaneously run more than two collector instances at combined 30k EPS. It is recommended to use the shortest fetch interval such as 30 seconds, for optimized performance. |
Includes Site Collector flows, out-of-the-box processors, groups, custom processors, other components, and integrations aimed at getting syslog logs from various sources and pushing the logs to New-Scale Security Operations Platform. For a successful use case implementation in Exabeam Cloud and easy monitoring of log sources, the Syslog collector helps to enable log onboarding from various sources. Ingests up to 10k EPS events per Site Collector instance with the average log size of 2.5k. For Syslog collector instances, each site Collector instance can ingest up to:
If you have multiple collector instances in the same Site Collector instance, the EPS will be split between the collector instances. To achieve higher EPS, create multiple Site Collector instances to split the traffic. | |
Includes a set of Site Collector flows, pre-built processors, groups, custom processors, other components, and integrations that pull logs in XML format from your Windows server and push the logs to New-Scale Security Operations Platform. The collector provides flexible template configuration capabilities to collect Windows events. A Windows Event Log Collector instance runs on its own Windows sever and can support up to 500 EPS at 10% CPU utilization, and 2k EPS at 40% CPU utilization. A single Site Collector instance runs up to 100 Windows Event Log Collector instances on a VM with common specifications. A single Site Collector instance runs up to 400 Windows Event Log Collector instances on a VM with enterprise specifications. It is recommended to set up one Windows Event Log Collector instance at a time, and not to set up multiple collector instances simultaneously. For optimal stability, it is recommended to create up to 80 Windows Event Log Collector instances for common specifications, and 300 Windows Event Log Collector instances for enterprise specifications. | |
Archive Windows Collector | The Archive Windows Collector collects log events from archived log files, *.gz, *.tar, *.tar.gz, *.gzip, *.rar, *.7z. The collector pulls logs in plain text format and pushes the logs to New-Scale Security Operations Platform. The collector provides flexible template configuration capabilities to collect Windows events. |
Archive Linux Collector | The Archive Linux Collector collects log events from archived log sources *.7z, *.arj, *.bzip2, *.cab, *.gzip, *.iso, *.lzh, *.rar, *.gz, *.tar, *.tar.gz, *.z, and *.zip. The collector pulls logs in plain text format and pushes the logs to New-Scale Security Operations Platform. The collector provides flexible template configuration capabilities to collect Linux events. |
Linux File Collector | The Linux File Collector retrieves logs natively from your Linux server, from most common text log files *.log, *.txt, and *.csv. It pulls single-line logs and pushes the logs to New-Scale Security Operations Platform. The collector provides flexible template configuration capabilities to collect Linux events. |
Windows File Collector | The Windows File Collector retrieves logs natively from your Windows server, from most common text log files *.log, *.txt, and *.csv. It pulls single-line logs and pushes the logs to New-Scale Security Operations Platform. The collector provides flexible template configuration capabilities to collect Windows events. |
Note
Site Collectors app maintains a balanced compression ratio and speed, and uses gzip compression mode. To enable you to enhance data throughput in the network by decreasing the data size, Site Collectors use 4-10x data compression rate for log data and 3-4x data compression rate for context data. The compression ratio varies per log source type.
Using an external load balancer, the Syslog data can be load balanced to ensure that the EPS is evenly distributed, and log collection is not impacted during scheduled updates. It is recommended that you deploy at least 2 site collector instances per load balancer for optimum performance. TCP load balancing is required for syslog.
Data at rest is encrypted.
A single Site Collector instance runs up to 100 Windows Event Log Collector instances on a VM with common specifications and 400 Windows Event Log Collector instances on a VM with enterprise specifications. For optimal stability, it is recommended to use 80 Windows Event Log Collector instances on a VM with common specifications and 300 Windows Event Log Collector instances on a VM with enterprise specifications.
