- Site Collector Overview
- Get Started with Site Collectors
- Install Site Collector
- Set Up Collectors
- Sign Up for the Early Access Program: Site Collectors
- Choose the Right Collector based on Data Sources
- Set Up Archive Windows Collector
- Set Up Archive Linux Collector
- Set Up EStreamer Collector
- Set Up Fortinet Collector
- Set Up IBM Security QRadar Collector
- Set Up Kafka Collector
- Set Up Splunk Collector
- Set Up Linux File Collector
- Set Up Microsoft SQL Collector
- Set Up MySQL Collector
- Set Up Oracle Collector
- Set Up Syslog Collector
- Set Up Windows Active Directory Collector
- Set Up Windows Event Log Collector
- Set Up Windows File Collector
- Manage Site Collectors
- Apply Antivirus Exclusions
- Migrate to the New-Scale Site Collectors Service
- Modify Collector Configuration
- Modify a Site Collector Instance
- Manage Templates
- Monitor Log Sources
- Add Filters to Set Egress Log Filtering Conditions
- New Site Collector Management Service NGSCD
- Regenerate Certificates for Collectors
- Upgrade the Site Collector
- Upgrade the Site Collector Specifications
- Vulnerability Remediation Policy
- Site Collector Monitoring
- Troubleshoot the Site Collector
- Pre-checks failed during Site Collector installation and upgrade
- Site Collector UI shows the status INSTALLATION_ERROR
- Download Support Packages for Troubleshooting
- How to reboot the Virtual Machine (VM) successfully to apply security updates?
- What information must be added while creating a support ticket to resolve an issue?
- Site Collector UI is not displaying the heartbeats
- Splunk Collector can't be set up
- Splunk Collector is set up however, logs are not reaching DL/AA
- Only a few of the installed Splunk Collectors are processing logs or EPS has dropped by 50% as compared to last hour
- The Windows Active Directory Collector (formerly known as LDAP Collector) is set up, however, the context data is not reaching DL/AA
- The Windows Active Directory Collector (formerly known as LDAP Collector) is stuck in the ‘Update’ mode after deployment
- Installation is initiated; however, the collector shows the status as ‘Setting Up’ for some time
- Data Lake and Advanced Analytics Does Not Show Context Data
- Context Data from Windows Active Directory Collector is Segmented
- Minifi Permission Denied - Logback.xml File Missing and Config File Update - Failed Error Occurred while Installing the Windows Event Log Collector
- Where should I upload proxy certificates if I am running proxy with TLS interception?
- How to upgrade Linux collector instance?
Set Up Linux File Collector
Set up the Linux File Collector to retrieve logs natively from your Linux server, from most common text log files *.log, *.txt, and *.csv. The Linux File Collector is a set of Site Collector flows, pre-built processors, groups, custom processors, other components, and integrations that pull single-line logs and push the logs to New-Scale Security Operations Platform. The collector provides flexible template configuration capabilities to collect Linux events.
Tip
If you configure a Linux File Collector instance for a Site Collector instance which was created using a hostname, you may get a 'Request timed out' error while establishing communication with the host VM from a Linux VM. To avoid the 'Request timed out' error and ‘Setup error’, ensure that you complete the following steps on your Linux VM.
Type ping hostnname_of_site_collector in your Linux command prompt. If this command succeeds, proceed with installing a Linux File Collector for this Site Collector instance. If you get a ‘Request timed out’, or ‘Cannot resolve host’ or ‘Unknown host’ error, use the following steps.
Open the hosts file that maintains mapping between hostname and IP_address, located at: \etc\hosts, using Notepad.
Add a new entry with your hostname and IP address at the end of the file for example, hostnname_of_site_collector ip_address
Save the hosts file.
Proceed to install a Linux File Collector instance for this Site Collector instance.
To set up a Linux File Collector:
Log in to the New-Scale Security Operations Platform with your registered credentials.
Navigate to Collectors > Site Collectors.
Ensure that Site Collector 1.16 and later version is installed and in running state.
On the Site Collector page, click the Collectors Library tab, then click Linux File.
In the Definition section, enter the required information as follows.
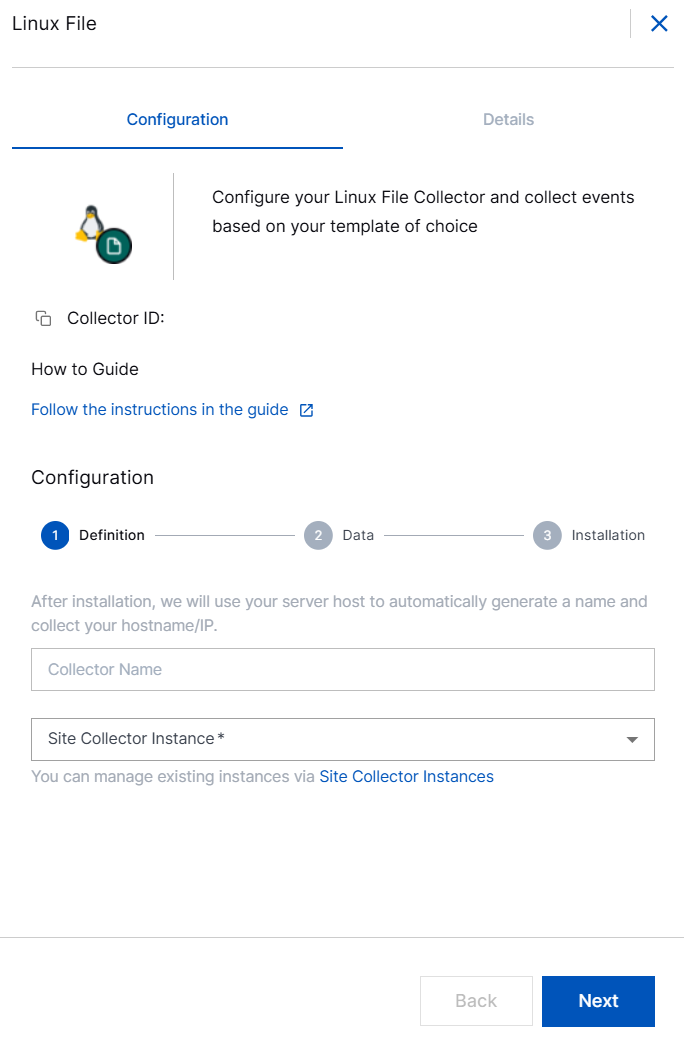
Collector Name – Site Collector generates a name for the Linux File collector based on your hostname.
Site Collector Instance – Select the site collector instance for which you want to set up the Linux File Collector.
Fetch Historical Data – Select this option for the collector to fetch log files that were created prior to the creation of the collector.
Click Next.
In the Data section, set up the Linux File template while configuring the collector. After you create a template, you can reuse the template for other collector instances or create a new template each time you set up a new Linux File Collector.
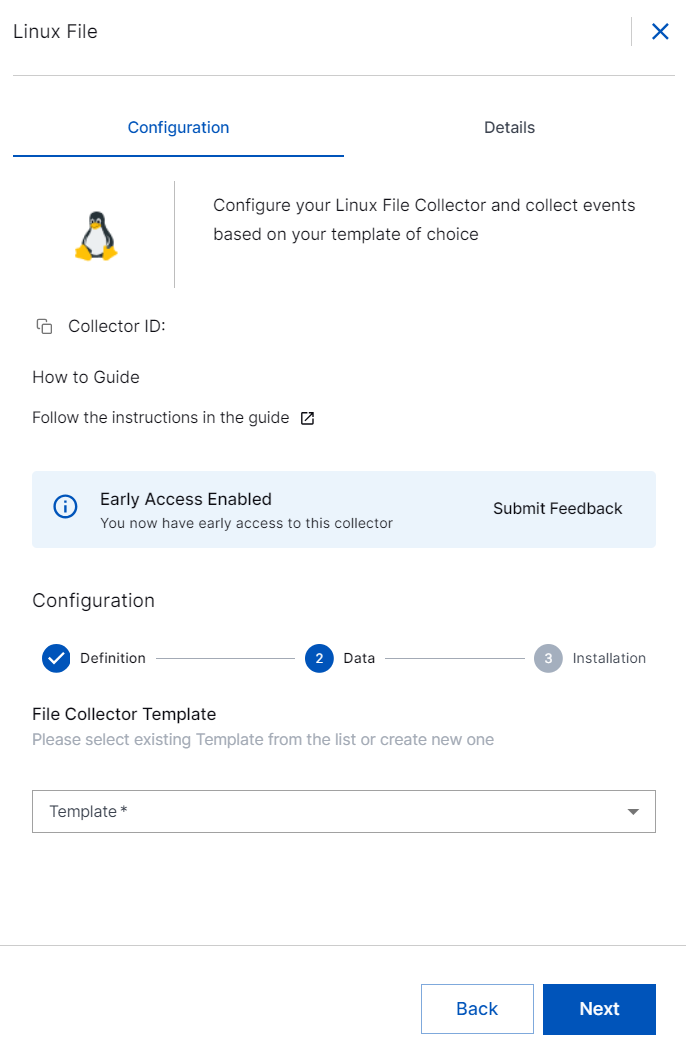
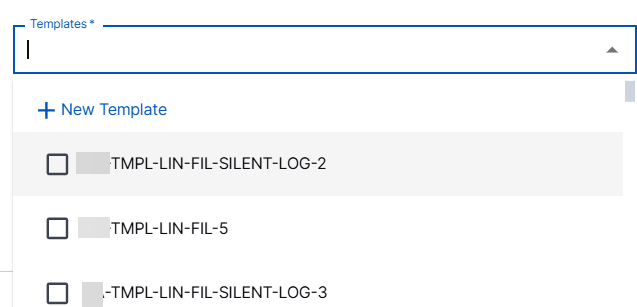
File Collector Template – Select a preconfigured template to filter logs, or, create a new template. Templates enable you to filter logs by file names.
You can select one or up to five preconfigured templates. If you select templates with conflicting conditions, the collector instance may pull duplicate data. To avoid data duplication, it is recommended to create templates with different conditions.
To create a new Linux File template:
In the Templates list, click New File Collector Template.
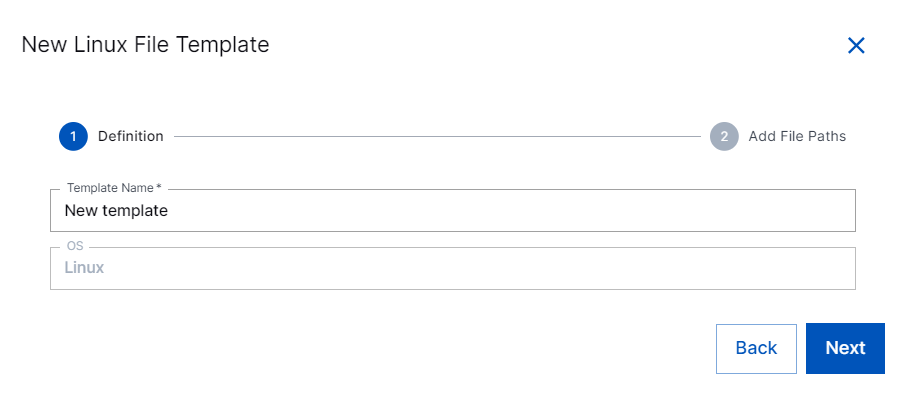
In the Template Name field, specify a name for the new Linux File template.
In the Add File Paths section, for filtering logs, enable the log fields that you want to use by entering regex.
The collector supports searching for log files across subdirectories which brings comprehensive log file collection by traversing and retrieving logs from nested directory structures.
Include – Enter regex for the file names or paths to be included in log collection.
For example, you can enter a file path with wildcard characters such as,
/var/log/*.logand/opt/exabeam/logs/*.txt.Here are the examples of advanced log filtering.
Example 1: If you include
/opt/exabeam/logs/*.txtin your regex, the collector searches for all files and subdirectories under /opt/exabeam/logs for files with the .txt suffix.Example 2: If you include
/opt/exabeam/logs/*in your regex, the collector configuration comprehensively processes all files and subdirectories within /opt/exabeam/logs, ensuring that every file in the specified directory and its nested structures is included in the processing.Exclude – Enter regex for the file names or paths to be rejected while collecting logs. The collector collects all the security events from the specified log name excluding the events or file names listed in this section.
For example, you can enter regex for exclude condition for excluding files or folders in the context of include condition:
c:\exabeam\logs\*.txt. Based on this regex, the collector ignores .txt logs.
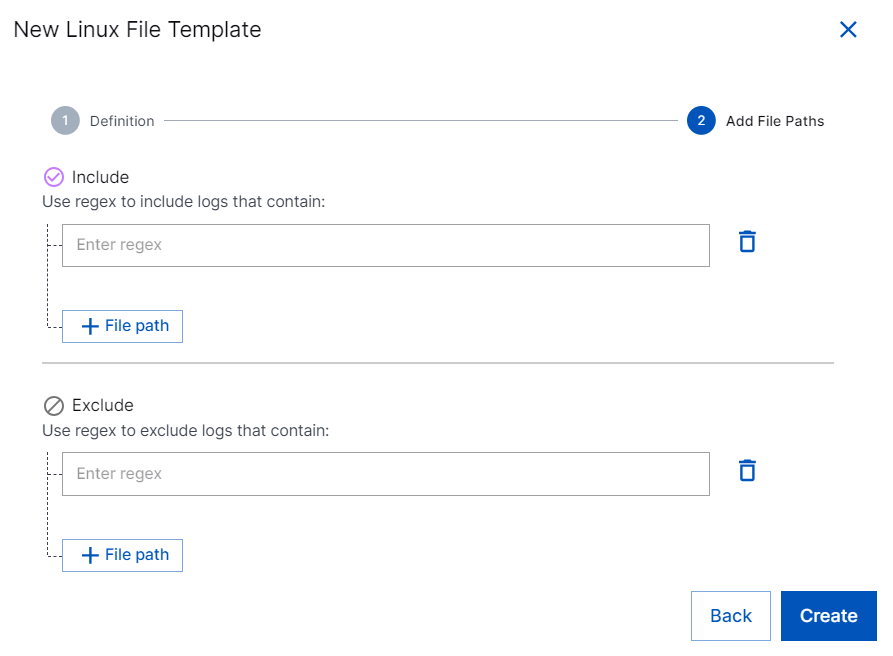
After setting the filters, click Create.
In the Installation section, copy the scripts and download certificates as follows.
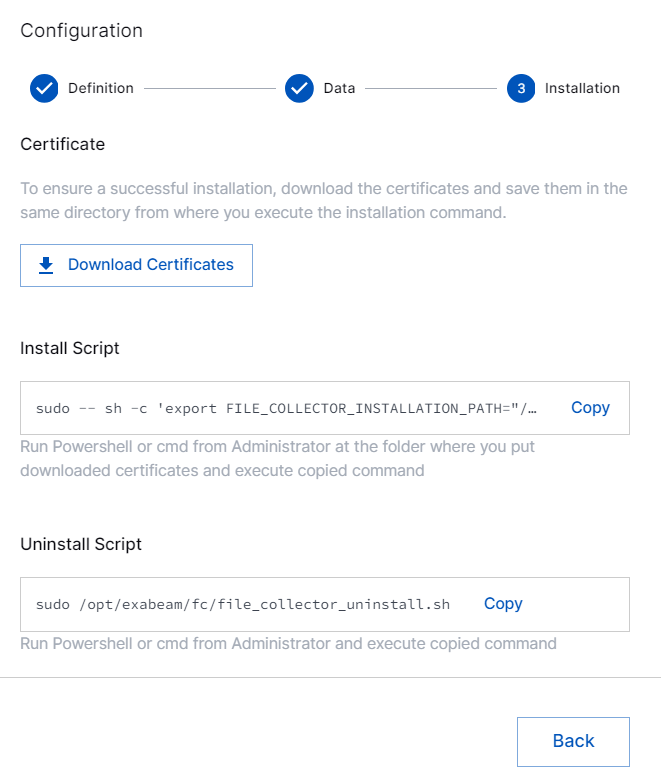
Certificate – Click Download Certificate to download the certificates. After you download the certificates, ensure that you save the certificates in the same directory from where you execute the Linux File Collector installation command.
Install Script – Copy the Install script. Paste the script in shell or terminal as an administrator where you put downloaded certificates. Then, run the copied command to install the Linux File collector.
Uninstall Script – To uninstall the Linux File collector, copy and run the script using shell or terminal as an administrator. You must execute the script on the Linux server.
Verify that the Collector installed. After you run the Install script on your Linux server, you get a confirmation message about successful collector installation and the Collector instance is listed in the Overview section on the user interface.
The Linux File Collector is set up and is ready to pull logs from source files based on the template configuration from your Linux server.
After the Linux collector is set up, Site Collector Core starts pulling logs periodically based on your template configuration and uploads logs to New-Scale Security Operations Platform. If the Linux server is not available, Site Collector core resumes pulling logs from the place where it stopped.
An antivirus software such as Crowdstrike Falcon Sensor may block arbitrary binary execution which may lead to installation failure. Ensure that you provide necessary permissions to execute the binary file by contacting your support team.
In case of installation failure, the collector is disabled, and the configuration is saved. You can check the status of the collector on the user interface or using the support package.
Note
The supported operating systems are RedHat 7, 8, and 9, and Ubuntu 18.04, 20.04, 22.04, and 24.04.
The Linux File Collector supports a maximum of 500 EPS for an average log size of 2.5Kb on a VM with common specifications. Each collector instance can process up to 1GB of logs per hour, with a limit of 20 files being processed in parallel.
For a VM with enterprise specifications, the collector provides 500 EPS for an individual collector at 10% CPU usage and 1800 EPS at 40% CPU usage, for average log size 2.5Kb. For optimal performance and stability it is recommended to create up to 300 collectors.
The agent-based collectors use mutual TLS (mTLS) for authentication for installation, which requires the collector to connect using actual IP address of Site Collector to establish a secure connection. Network Address Translation (NAT) is not supported because it causes authentication failures and prevents installation. This restriction applies irrespective of proxy or VPN usage. Similarly, any configuration that involves NAT or TLS inspection—including those without proxy or VPN—will result in authentication failure and installation errors.
