- Case Manager Release Notes
- Get Started with Case Manager
- Configure Case Manager Settings
- Investigate a Security Incident
- Manually Create an Incident
- Edit an Incident
- Delete an Incident
- Manually Add an Entity
- Manually Add an Artifact
- Delete an Entity or Artifact
- Add Advanced Analytics Evidence to a Case Manager Incident
- Manage Tasks During an Investigation
- Send Messages from an Incident
- Filter Incidents
- Search for an Incident
- Sort Incidents
- Export Incidents
What's New
What's New in i63
Case Manager in Dashboard
Dashboards has replaced Case Manager Metrics. In Dashboards, create visualizations using Case Manager data and get high-level insights into your Case Manager activity with a pre-built dashboard.
A pre-built Case Manager dashboard, the Case Management Overview dashboard, replaces most pre-built Case Manager metrics. The Hours Saved and cost savings metrics are deprecated. With a pre-built dashboard, you easily visualize and report on your team's workload and performance without configuring your own dashboards.
Exabeam Documentation: Case Management Overview Dashboard
What's New in i62
Role-Based Incident Access Restriction
Extend role-based access control to incidents.
In an incident's Restrict To settings, you can select specific roles so only people with those roles can access the incident. You can select out-of-the-box roles or custom roles you created.
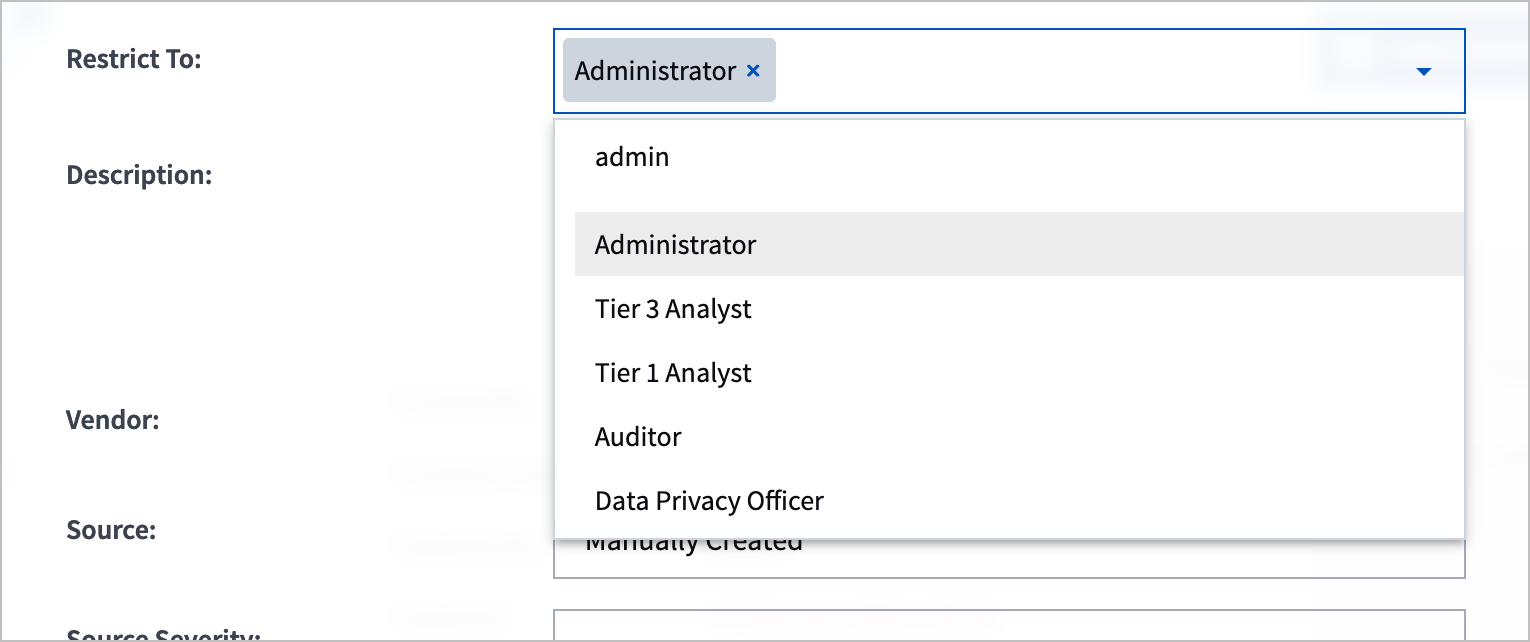
Exabeam Documentation: Manually Create an Incident
Exabeam Documentation: Edit an Incident
What's New in i61
Incident Visibility for SOC Managers
With a new permission, SOC managers can view all Case Manager incidents.
Anybody with View Restricted Incidents permissions can bypass an incident's Restrict to settings and view all incidents. This permission helps SOC managers respond to audit and compliance requests.
The Administrator, Auditor, and Data Privacy Officer out-of-the-box roles have View Restricted Incidents permissions. You can add this permission to your own custom roles.
Exabeam Documentation: Default Roles
Microsoft OAuth2.0 Code Grant Change
To better secure data from email ingest and incident email, Microsoft Exchange Online uses OAuth2.0 authentication with the authorization code flow grant.
Instead of relying on a single client ID and client secret, the authorization code grant gives only certain accounts access to your Microsoft Azure Activity Directory application. Every time you configure email ingest or incident email, you must log in to an authorized account.
After you upgrade to Case Manager i61, ensure that you complete new prerequisites for configuring Microsoft Exchange Online with OAuth2.0 authentication, including restricting your application to the emails you use for email ingest and incident email, adding new permissions, and adding redirect URIs. You must also reconfigure email ingest and incident email.
Exabeam Documentation: Prerequisites for Configuring Microsoft Exchange Online with OAuth2.0 Authentication
Exabeam Documentation: Configure Email Ingest
Exabeam Documentation: Configure Incident Email Communication
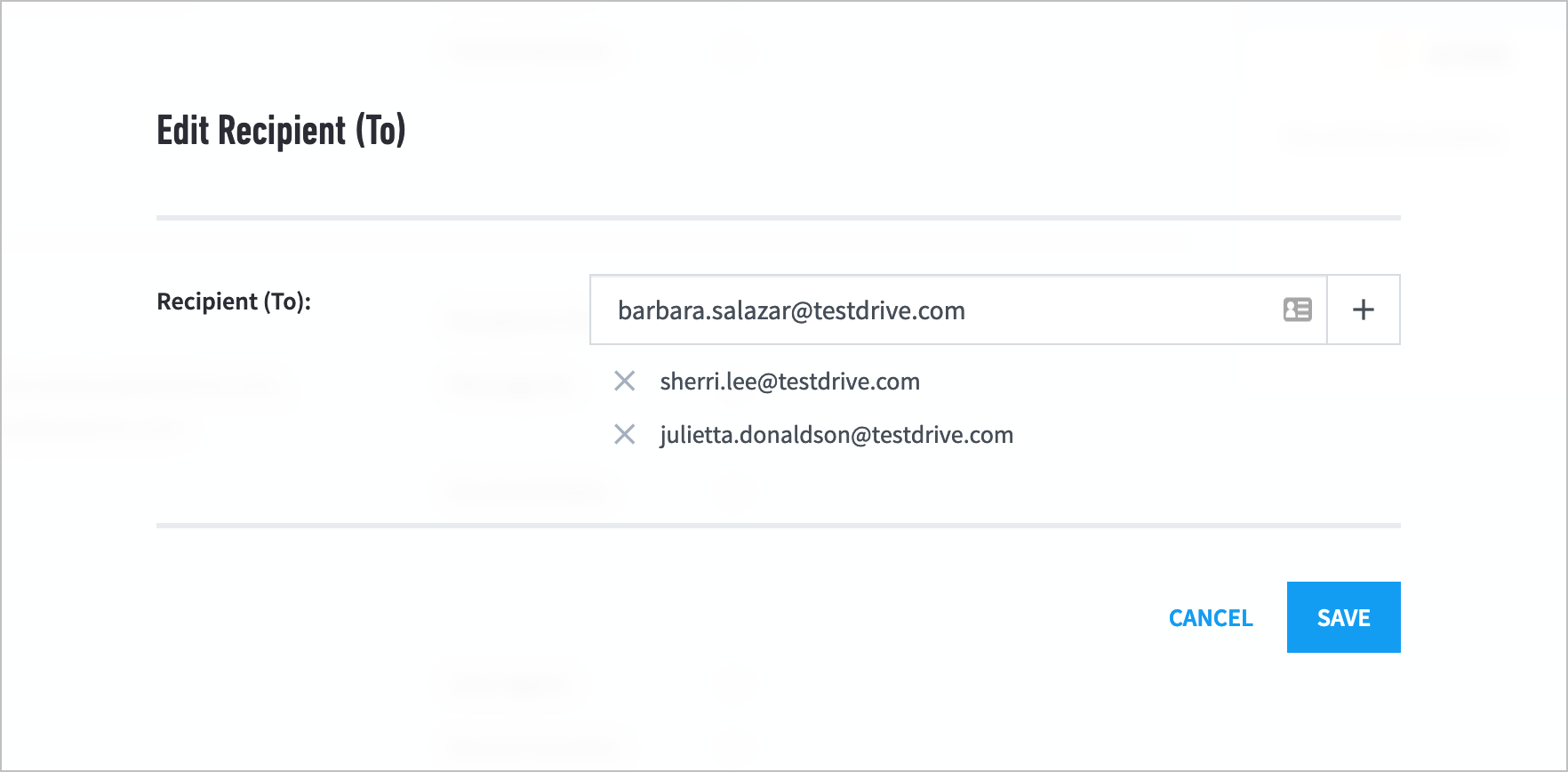
Multiple Value Selection for Phishing Incident Fields
Select multiple values for certain incident fields under the Phishing incident type so your Case Manager incident better reflects your investigation.
By default, you can enter multiple values for the Attachment Name, CC, Recipient (To), and Sender (From) incident fields so they more accurately represent your investigation's evidence. For example, if an email has multiple recipients, you can enter multiple values for the Recipient incident field.
What's New in i60
Task and Incident Fields Completion Enforcement for Thorough Investigations
Ensure your team completes all tasks and collects all necessary evidence for an incident.
To ensure your team completes all tasks, you can no longer close an incident if any required tasks are open or required incident fields are empty. If you close an incident that has open required tasks or empty required incident fields, you receive an error.
Task Assignee Restriction
Restrict access to sensitive information in incidents and prevent tasks from being assigned to unauthorized team members.
You can no longer assign tasks to people restricted from accessing an incident. Open tasks previously assigned to people restricted from an incident are re-assigned to Unassigned.
Restricted Editing for Closed Incidents
If an incident's status is Closed, you can't edit the incident. If you try to edit the incident, you receive an error.
To edit a closed incident, change the incident to another status, like Open, In Progress, Pending, or Resolved.
Exabeam Documentation: Edit an Incident
What's New in i59
Apache Log4j Security Patch
Note
We updated the release notes to include information about a security patch to the Exabeam platform.
A critical vulnerability in software using Apache Log4j affected Elasticsearch in Case Manager. This vulnerability has been patched. Learn more about Exabeam's response to the vulnerability on the Exabeam Community.
Generic Incident Type Customization
Get more control over what information is displayed in every incident.
To ensure certain information is added to every incident, add custom incident fields to the Generic incident type. You an also customize the Generic incident type's layout to rearrange how the incident fields are displayed in the incident. You can't remove the default incident fields that come with the incident type.
Exabeam Documentation: Generic Incident Type
What's New in i58
Out-of-the-Box Incident Types for Exabeam Threat Detection, Investigation, and Response (TDIR) Use Case Packages
Make your investigations more consistent and complete with new out-of-the-box incident types aligned with TDIR Use Case Packages: Compromised Insiders, Malicious Insiders, and External Threats.
Now, you can use an expanded collection of out-of-the-box incident types. These incident types ensure that you collect the appropriate evidence and define clear response plans for every use case.
Most incident types come with specific incident fields and tasks. You can edit the incident fields and tasks, rearrange them, or create custom incident fields and tasks for any out-of-the-box incident types to better suit your needs.
Exabeam Documentation: Out-of-the-Box Incident Types for Compromised Insiders Use Cases
Exabeam Documentation: Out-of-the-Box Incident Types for Malicious Insiders Use Cases
Exabeam Documentation: Out-of-the-Box Incident Types for External Threats Use Cases
What's New in i57
This release does not include new features for Case Manager.
