- Advanced Analytics
- Understand the Basics of Advanced Analytics
- Configure Log Management
- Set Up Admin Operations
- Set Up Authentication and Access Control
- Additional Configurations
- Configure Rules
- Exabeam Threat Intelligence Service
- Threat Intelligence Service Prerequisites
- View Threat Intelligence Feeds
- Threat Intelligence Context Tables
- View Threat Intelligence Context Tables
- Assign a Threat Intelligence Feed to a New Context Table
- Create a New Context Table from a Threat Intelligence Feed
- Check ExaCloud Connector Service Health Status
- Exabeam Cloud Telemetry Service
- Manage Security Content in Advanced Analytics
- Health Status Page
Exabeam Threat Intelligence Service
The Exabeam Threat Intelligence Service delivers up-to-date threat indicators, on a daily basis, to Advanced Analytics deployments. Threat indicator data is stored in context tables that are associated with each feed. These threat indicators provide enhanced data based on curated threat intelligence.
The table below lists the categories of threat indicators provided by each threat intelligence feed and the rules that leverage each feed.
Note
All of the threat intelligence feeds, except the TOR network category, provide curated threat intelligence from ZeroFox. The TOR network feed is an open source data feed.
IoC Category | Rules |
|---|---|
Ransomeware IP IP addresses associated with ransomware attacks |
|
Threat IP IP addresses associated with ransomware or malware attacks |
|
Reputation Domain Domain names and URLs associated with sites that often contain malware, drive-by compromises, and more |
|
Web Phishing Domain names associated with phishing or ransomware | WEB-UD-Phishing |
TOR IP IP addresses associated with the TOR network |
|
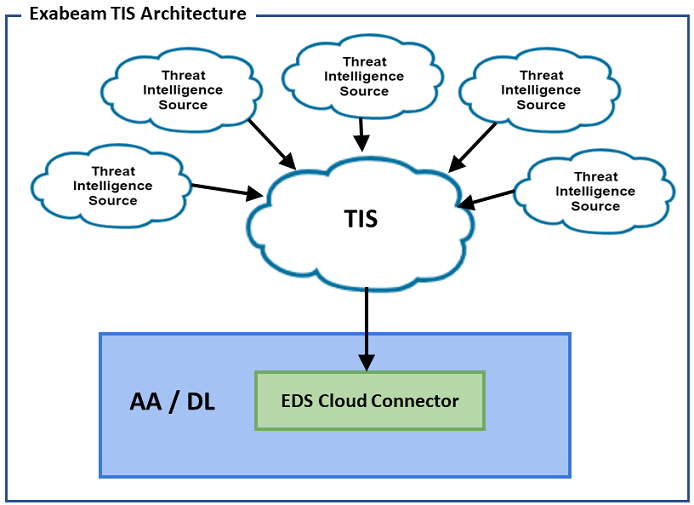
Cloud-delivered deployments of Advanced Analytics and Data Lake connect to the Threat Intelligence Service (TIS) through an Exabeam Data Service (EDS) cloud connector, as shown in the image below. The cloud connector service provides authentication and establishes a secure connection to the Threat Intelligence Service. The cloud connector service collects updated threat indicators from the Threat Intelligence Service and makes them available within Advanced Analytics and Data Lake on a daily basis.
 |
The Threat Intelligence Service does not require a separate license. It is bundled with Advanced Analytics deployments. Additional installation is not required.
For on-premise deployments of Advanced Analytics and Data Lake, threat indicators are downloaded directly from the Threat Intelligence Service on a daily basis.
For more information about the Threat Intelligence Service, contact your technical account manager.
