- Advanced Analytics
- Understand the Basics of Advanced Analytics
- Configure Log Management
- Set Up Admin Operations
- Set Up Authentication and Access Control
- Additional Configurations
- Configure Rules
- Exabeam Threat Intelligence Service
- Threat Intelligence Service Prerequisites
- View Threat Intelligence Feeds
- Threat Intelligence Context Tables
- View Threat Intelligence Context Tables
- Assign a Threat Intelligence Feed to a New Context Table
- Create a New Context Table from a Threat Intelligence Feed
- Check ExaCloud Connector Service Health Status
- Exabeam Cloud Telemetry Service
- Manage Security Content in Advanced Analytics
- Health Status Page
Cluster Authorization Token
The cluster authorization token is used to verify identities between clusters that have been deployed in phases as well as HTTP-based log collectors. Each peer cluster in a query pool must have its own token. You can set expiration dates during token creation or manually revoke tokens at any time.
To generate a token:
Navigate to Settings > Core > Admin Operations > Cluster Authorization Token.
The Cluster Authorization Token page is displayed.
In the Cluster Authorization Token page, click
 to open the Setup Token dialog box.
to open the Setup Token dialog box.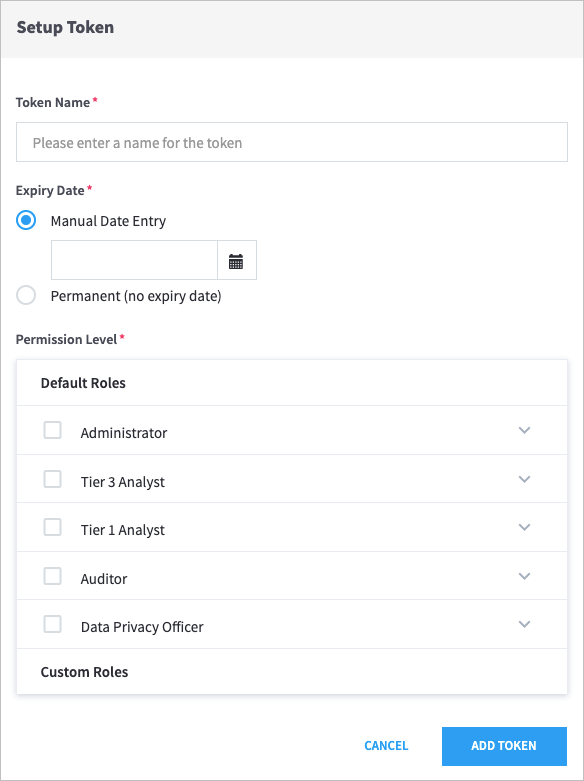
Enter a Token Name, and then select an Expiry Date.
Important
Token names can contain only letters, numbers, and spaces.
Select the Default Roles for the token.
Click Add Token.
Use this generated file to allow your APIs to authenticate by token. Ensure that your API uses
ExaAuthTokenin its requests. For curl clients, the request structure resembles the following:curl -H "ExaAuthToken:<generated_token>" https://<external_host>:<api_port>/<api_request_path>
