- Advanced Analytics
- Understand the Basics of Advanced Analytics
- Configure Log Management
- Set Up Admin Operations
- Set Up Authentication and Access Control
- Additional Configurations
- Configure Rules
- Exabeam Threat Intelligence Service
- Threat Intelligence Service Prerequisites
- View Threat Intelligence Feeds
- Threat Intelligence Context Tables
- View Threat Intelligence Context Tables
- Assign a Threat Intelligence Feed to a New Context Table
- Create a New Context Table from a Threat Intelligence Feed
- Check ExaCloud Connector Service Health Status
- Exabeam Cloud Telemetry Service
- Manage Security Content in Advanced Analytics
- Health Status Page
Manage Users
Understand the difference between Roles and Users. Configure the analysts that have access to the Exabeam User Interface, add the analyst's information, assign them roles, and set up user permissions and access based on your organization's needs.
Users
Users are the analysts that have access to the Exabeam UI to review and investigate activity. These analysts have specific roles, permissions, and can be assigned Exabeam objects within the platform. They also have the ability to accept sessions. Exabeam supports local authentication or authentication against an LDAP server.
Default Roles
Advanced Analytics includes preconfigured default roles with standard permission sets for common user types, such as analysts, administrators, and auditors.
Note
Default roles cannot be edited or deleted.
This role is intended for administrative access to Exabeam. Users assigned to this role can perform administrative operations on Exabeam, such as configuring the appliance to fetch logs from the SIEM, connecting to Active Directory to pull in contextual information, and restarting the analytics engine. The default admin credential belongs to this role. This is a predefined role provided by Exabeam and cannot be deleted.
Default permissions include:
Permission | Description |
|---|---|
Manage Users and Context Sources | Manage users and roles in the Exabeam Security Intelligence Platform, as well as the context sources used to enhanced the logs ingested (e.g. assets, peer groups, service accounts, executives). |
Manage context tables | Manage users, assets or other objects within Context Tables. |
Manage Content Packages | Users add/remove/configure content packages for automatic installation. |
View Metrics | View the IR Metrics page. |
Manage Data Ingest | Configure log sources and feeds and email-based ingest. |
Add IR comments | Add IR comments. |
Upload Custom Services | Upload custom actions or services. |
Create incidents | Create incidents. |
Delete incidents | Delete incidents. |
Manage Custom Services and Packages | User can manage custom services and related packages |
Manage Data Ingest | Configure log sources and feeds and email-based ingest. |
Manage ingest rules | Add, edit, or delete rules for how incidents are assigned, restricted, and prioritized on ingest. |
Manage Queues | Create, edit, delete, and assign membership to queues |
Manage Templates | Create, edit, or delete playbook templates. |
Manage Triggers | Create, update, or delete playbook triggers. |
Run Actions | Launch individual actions from the user interface. |
Manage Bi-directional Communication | Configure inbound and outbound settings for Bi-Directional Communications. |
Manage Incident Configuration | Users can manage the Incident Configurations including Incident Types, Fields, Layouts, and Checklists. |
Manage Playbooks | Create, update, or delete playbooks. |
Manage Services | Configure, edit, or delete services (3rd party integrations). |
Run Playbooks | Run a playbook manually from the workbench. |
Reset Incident Workbench | User can reset incident workbench |
All Admin Ops | Perform all Exabeam administrative operations such as configuring the appliance, connecting to the log repository and Active Directory, setting up log feeds, managing users and roles that access the Exabeam UI, and performing system health checks. |
View comments | View comments. |
View health | View health. |
View Raw Logs | View the raw logs that are used to built the events on AA timeline |
View Rules | View configured rules that determine how security events are handled |
View API | View API. |
View incidents | View incidents. |
View Metrics | View the IR Metrics page. |
Edit incidents | Edit an incident's fields, edit tasks, entities & artifacts. |
Manage Rules | Create/Edit/Reload rules that determine how security events are handled |
Bulk edit | Users can edit multiple incidents at the same time. |
Search Incidents | Can search keywords in IR via the search bar. |
Basic Search | Perform basic search on the Exabeam homepage. Basic search allows you to search for a specific user, asset, session, or a security alert. |
View Restricted Incidents | View incidents restricted to other users or groups. |
Users assigned to this role have only view privileges within the Exabeam UI. They can view all activities within the Exabeam UI, but cannot make any changes such as add comments or approve sessions. This is a predefined role provided by Exabeam.
Default permissions include:
Permission | Description |
|---|---|
View Comments | View comments |
View Activities | View all notable users, assets, sessions, and related risk reasons in the organization. |
View Global Insights | View the organizational models built by Exabeam. The histograms that show the normal behavior for all entities in the organization can be viewed. |
View Executive Info | View the risk reasons and the timeline of the executive users in the organization. You will be able to see the activities performed by executive users along with the associated anomalies. |
View Incidents | View incidents. |
View Infographics | View all the infographics built by Exabeam. You will be able to see the overall trends for the organization. |
View Insights | View the normal behaviors for specific entities within the organization. The histograms for specific users and assets can be viewed. |
Search Incidents | Can search keywords in Incident Responder via the search bar. |
Basic Search | Perform basic search on the Exabeam homepage. Basic search allows you to search for a specific user, asset, session, or a security alert. |
View Search Library | View the Search Library provided by Exabeam and the corresponding search results associated with the filters. |
Threat Hunting | Perform threat hunting on Exabeam. Threat hunting allows you to query the platform across a variety of dimension such as find all users whose sessions contain data exfiltration activities or a malware on their asset. |
View Restricted Incidents | View incidents restricted to other users or groups. |
Users assigned to this role are junior security analysts or incident desk responders who supports the day-to-day enterprise security operation and monitoring. This type of role will not be authorized to make any changes to Exabeam system except for making user, session and lockout comments. Users in this role cannot approve sessions or lockout activities. This is a predefined role provided by Exabeam.
Default permissions include:
Permission | Description |
|---|---|
Add Advanced Analytics Comments | Add comments for the various entities (users, assets and sessions) within Exabeam. |
Add Incident Responder Comments | Add Incident Responder comments. |
Create Incidents | Create incidents. |
Run Playbooks | Run a playbook manually from the workbench. |
Run Actions | Launch individual actions from the user interface. |
View comments | View comments. |
View Global Insights | View the organizational models built by Exabeam. The histograms that show the normal behavior for all entities in the organization can be viewed. |
View incidents | View incidents. |
View Infographics | View all the infographics built by Exabeam. You will be able to see the overall trends for the organization. |
View Activities | View all notable users, assets, sessions and related risk reasons in the organization. |
View Executive Info | View the risk reasons and the timeline of the executive users in the organization. You will be able to see the activities performed by executive users along with the associated anomalies. |
View Insights | View the normal behaviors for specific entities within the organization. The histograms for specific users and assets can be viewed. |
Users assigned to this role will be performing more complex investigations and remediation plans. They can review user sessions, account lockouts, add comments, approve activities and perform threat hunting. This is a predefined role provided by Exabeam and cannot be deleted.
Default permissions include:
Permission | Description |
|---|---|
Add Advanced Analytics Comments | Add comments for the various entities (users, assets and sessions) within Exabeam. |
Add Incident Responder Comments | Add Incident Responder comments. |
Upload Custom Services | Upload custom actions or services. |
Create incidents | Create incidents. |
Delete incidents | Delete incidents. |
Manage Playbooks | Create, update, or delete playbooks. |
Manage Queues | Create, edit, delete, and assign membership to queues |
Manage Services | Configure, edit, or delete services (3rd party integrations). |
Manage Triggers | Create, update, or delete playbook triggers. |
Run Actions | Launch individual actions from the user interface. |
Manage Bi-directional Communication | Configure inbound and outbound settings for Bi-Directional Communications. |
Manage Data Ingest | Configure log sources and feeds and email-based ingest. |
Manage ingest rules | Add, edit, or delete rules for how incidents are assigned, restricted, and prioritized on ingest. |
Manage Templates | Create, edit, or delete playbook templates. |
Run Playbooks | Run a playbook manually from the workbench. |
View Activities | View all notable users, assets, sessions and related risk reasons in the organization. |
View Comments | View comments. |
View Executive Info | View the risk reasons and the timeline of the executive users in the organization. You will be able to see the activities performed by executive users along with the associated anomalies. |
View Global Insights | View the organizational models built by Exabeam. The histograms that show the normal behavior for all entities in the organization can be viewed. |
View Infographics | View all the infographics built by Exabeam. You will be able to see the overall trends for the organization. |
View Rules | View configured rules that determine how security events are handled. |
View Insights | View the normal behaviors for specific entities within the organization. The histograms for specific users and assets can be viewed. |
Bulk Edit | Users can edit multiple incidents at the same time. |
Delete entities and artifacts | Users can delete entities and artifacts. |
Manage Watchlist | Add or remove users from the Watchlist. Users that have been added to the Watchlist are always listed on the Exabeam homepage, allowing them to be scrutinized closely. |
Approve Lockouts | Accept account lockout activities for users. Accepting lockouts indicates to Exabeam that the specific set of behaviors for that lockout activity sequence are whitelisted and are deemed normal for that user. |
Accept Sessions | Accept sessions for users. Accepting sessions indicates to Exabeam that the specific set of behaviors for that session are whitelisted and are deemed normal for that user. WarningThis permission should be given only sparingly, if at all. Accepting sessions is not recommended. The best practice for eliminating unwanted alerts is through tuning the rules and/or models. |
Edit incidents | Edit an incident's fields, edit entities & artifacts. |
Sending incidents to Incident Responder | Send incidents to Incident Responder. |
Basic Search | Perform basic search on the Exabeam homepage. Basic search allows you to search for a specific user, asset, session, or a security alert. |
Search Incidents | Can search keywords in IR via the search bar. |
Threat Hunting | Perform threat hunting on Exabeam. Threat hunting allows you to query the platform across a variety of dimensions such as find all users whose sessions contain data exfiltration activities or a malware on their asset. |
Manage Search Library | Create saved searches as well as edit them. |
View Search Library | View the Search Library provided by Exabeam and the corresponding search results associated with the filters. |
This role is needed only when the data masking feature is turned on within Exabeam. Users assigned to this role are the only users that can view personally identifiable information (PII) in an unmasked form. They can review user sessions, account lockouts, add comments, approve activities and perform threat hunting. This is a predefined role provided by Exabeam.
See Mask Data Within the Advanced Analytics UI for more information on this feature.
Default permissions include:
Permission | Description |
|---|---|
Add Advanced Analytics Comments | Add comments for the various entities (users, assets and sessions) within Exabeam. |
View comments | View comments. |
View Global Insights | View the organizational models built by Exabeam. The histograms that show the normal behavior for all entities in the organization can be viewed. |
View incidents | View incidents. |
View Infographics | View all the infographics built by Exabeam. You will be able to see the overall trends for the organization. |
View Activities | View all notable users, assets, sessions and related risk reasons in the organization. |
View Executive Info | View the risk reasons and the timeline of the executive users in the organization. You will be able to see the activities performed by executive users along with the associated anomalies. |
View Insights | View the normal behaviors for specific entities within the organization. The histograms for specific users and assets can be viewed. |
Manage Watchlist | Add or remove users from the Watchlist. Users that have been added to the Watchlist are always listed on the Exabeam homepage, allowing them to be scrutinized closely. |
Sending incidents to Incident Responder | Sending incidents to Incident Responder. |
Accept Sessions | Accept sessions for users. Accepting sessions indicates to Exabeam that the specific set of behaviors for that session are whitelisted and are deemed normal for that user. |
Basic Search | Perform basic search on the Exabeam homepage. Basic search allows you to search for a specific user, asset, session, or a security alert. |
Threat Hunting | Perform threat hunting on Exabeam. Threat hunting allows you to query the platform across a variety of dimensions such as find all users whose sessions contain data exfiltration activities or a malware on their asset. |
Manage Search Library | Create saved searches as well as edit them |
View Search Library | View the Search Library provided by Exabeam and the corresponding search results associated with the filters. |
View Unmasked Data (PII) | Show all personally identifiable information (PII) in a clear text form. When data masking is enabled within Exabeam, this permission should be enabled only for select users that need to see PII in a clear text form. |
View Restricted Incidents | View incidents restricted to other users or groups. |
Create a Custom User Role
If the preconfigured default roles do not meet all your needs, you can create your own roles.
To add a new role:
Click Settings
 , and then click Analytics > Exabeam User Management > Roles.
, and then click Analytics > Exabeam User Management > Roles.The User Management page opens with the Roles tab selected.
Click Create Role.
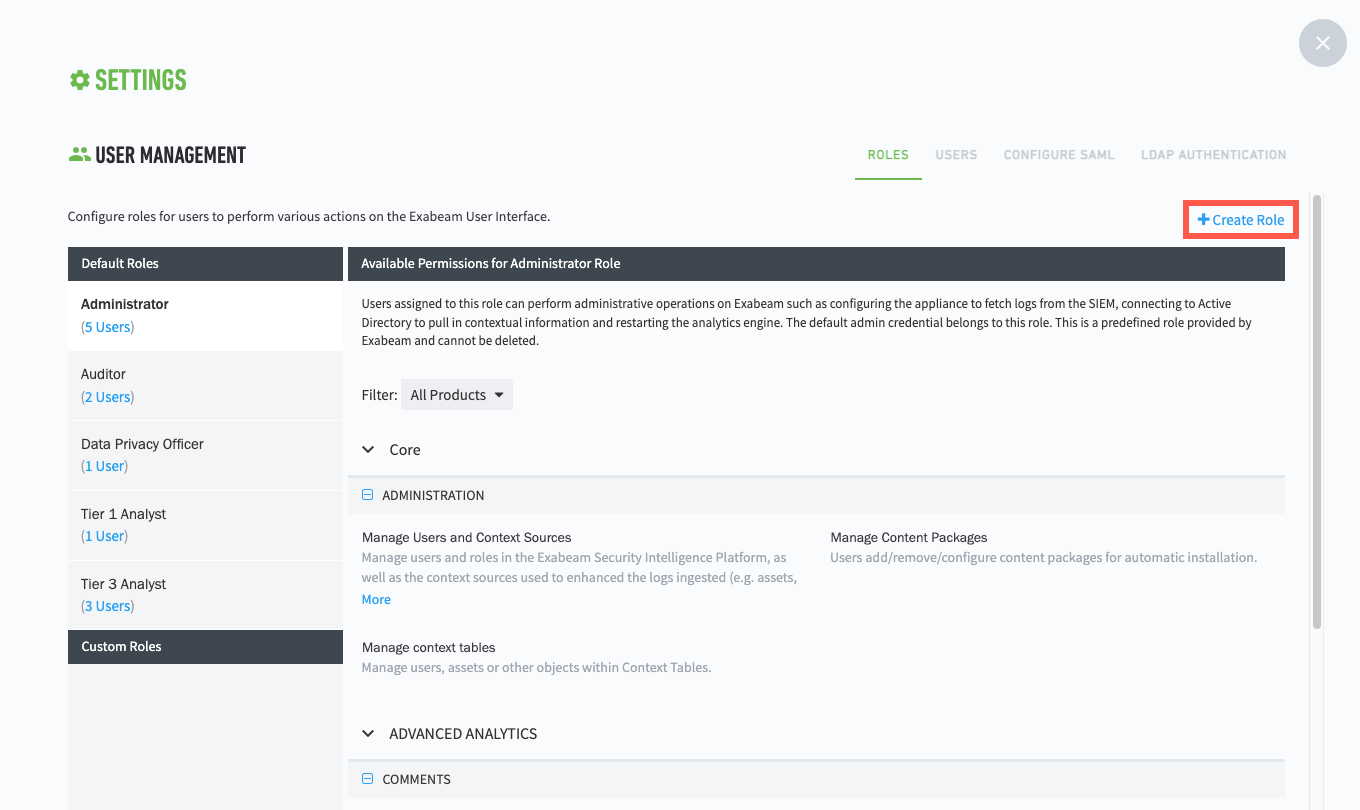
In the Create a new role dialog box, enter a Role name and ensure that the Advanced Analytics tab is selected.
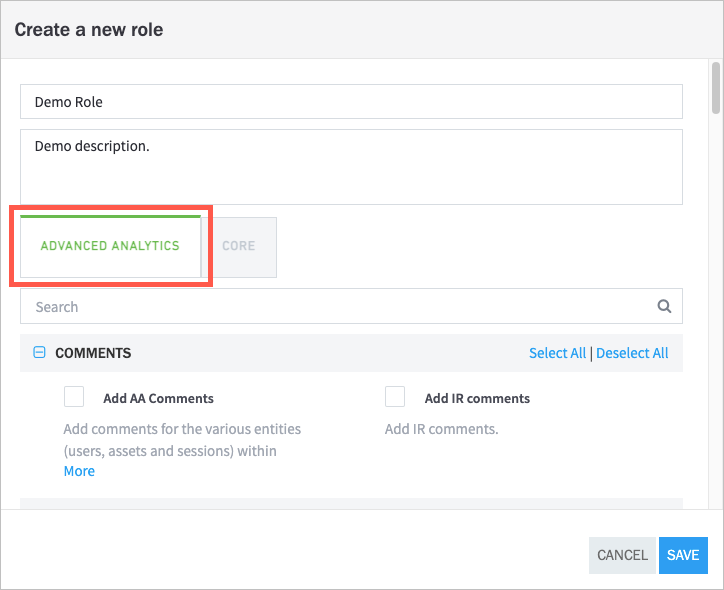
Select the permissions that you want to assign to the role.
To quickly find specific permissions, use the search bar. Otherwise, scroll down to view the available permissions.
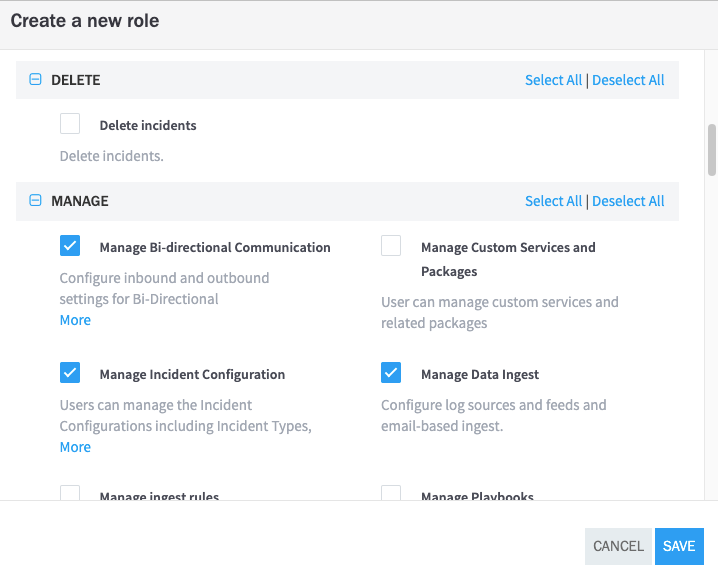
When you are finished, click Save.
The new role appears in the list of Custom Roles on the Roles tab of the User Management page. From the Users tab, you can assign the role to both new and existing users.
Add an Exabeam User
Navigate to Settings > Exabeam User Management > Users.
Click Add User.
Fill the new user fields and select role(s), and then click SAVE.
Your newly created user should appear in the Users UI.
User Password Policies
Exabeam users must adhere to the following default password security requirements:
Passwords must:
Be between 8 to 32 characters
Contain at least one uppercase, lowercase, numeric, and special character
Contain no blank space
User must change password every 90 days
New passwords cannot match last 5 passwords
SHA256 hashing is applied to store passwords
Only administrators can reset passwords and unblock users who have been locked out due to too many consecutive failed logins
If you need to modify the default password policies, contact Exabeam Customer Support.
