- Cloud Collectors Overview
- Administration
- Administrative Access
- Shareable Service Accounts
- Add Accounts for AWS Cloud Collectors
- Add Accounts for Cisco Duo Cloud Collector
- Add Accounts for Google Cloud Collectors
- Add Accounts for Microsoft Cloud Collectors
- Add Accounts for Okta Cloud Collectors
- Add Accounts for Salesforce Cloud Collectors
- Add Accounts for Splunk Cloud Collectors
- Add Accounts for Trend Micro Cloud Collectors
- Add Accounts for Wiz
- Define a Unique Site Name
- Sign Up for the Early Access Program
- Supported Cloud Collectors
- Onboard Cloud Collectors
- Abnormal Security Cloud Collector
- Anomali Cloud Collector
- AWS CloudTrail Cloud Collectors
- AWS CloudWatch Cloud Collector
- AWS CloudWatch Alarms Cloud Collector
- AWS GuardDuty Cloud Collector
- AWS S3 Cloud Collector
- AWS Security Lake Cloud Collector
- AWS SQS Cloud Collector
- Azure Activity Logs Cloud Collector
- Azure Blob Storage Cloud Collector
- Azure Log Analytics Cloud Collector
- Azure Event Hub Cloud Collector
- Azure Storage Analytics Cloud Collector
- Azure Virtual Network Flow Cloud Collector
- Box Cloud Collector
- Broadcom Carbon Black Cloud Collector
- Cato Networks Cloud Collector
- ChatGPT Enterprise Cloud Collector
- Cisco Duo Cloud Collector
- Cisco Meraki Cloud Collector
- Cisco Secure Endpoint Cloud Collector
- Cisco Umbrella Cloud Collector
- Cloudflare Cloud Collector
- Cribl Cloud Collector
- CrowdStrike Cloud Collectors
- Cylance Protect (now Arctic Wolf) Cloud Collector
- DataBahn Cloud Collector
- Dropbox Cloud Collector
- GCP Cloud Logging Cloud Collector
- GCP Pub/Sub Cloud Collector
- GCP Security Command Center Cloud Collector
- Gemini Enterprise Cloud Collector
- GitHub Cloud Collector
- Gmail BigQuery Cloud Collector
- Google Workspace Cloud Collector
- LastPass Cloud Collector
- Microsoft Defender XDR (via Azure Event Hub) Cloud Collector
- Microsoft Entra ID Context Cloud Collector
- Microsoft Entra ID Logs Cloud Collector
- Microsoft 365 Exchange Admin Reports Cloud Collector
- Supported Sources from Microsoft 365 Exchange Admin Reports
- Migrate to the Microsoft 365 Exchange Admin Reports Cloud Collector
- Prerequisites to Configure the Microsoft 365 Exchange Admin Reports Cloud Collector
- Configure the Microsoft 365 Exchange Admin Reports Cloud Collector
- Troubleshooting the Microsoft 365 Exchange Admin Reports Cloud Collector
- Microsoft 365 Management Activity Cloud Collector
- Microsoft Security Alerts Cloud Collector
- Microsoft Sentinel (via Event Hub) Cloud Collector
- Mimecast Cloud Collector
- Mimecast Incydr Cloud Collector
- Netskope Alerts Cloud Collector
- Netskope Events Cloud Collector
- Okta Cloud Collector
- Okta Context Cloud Collector
- Palo Alto Networks Cortex Data Lake Cloud Collector
- Palo Alto Networks XDR Cloud Collector
- Progress ShareFile Cloud Collector
- Proofpoint On-Demand Cloud Collector
- Proofpoint Targeted Attack Protection Cloud Collector
- Qualys Cloud Collector
- Recorded Future Cloud Collector
- Recorded Future Context Cloud Collector
- Rest API Cloud Collector
- S2W Threat Intelligence Cloud Collector
- Salesforce Cloud Collector
- Salesforce EventLog Cloud Collector
- SentinelOne Alerts Cloud Collector
- SentinelOne Cloud Funnel Cloud Collector
- SentinelOne Threats Cloud Collector
- SentinelOne Cloud Collector
- ServiceNow Cloud Collector
- Slack Cloud Collector
- Snowflake Cloud Collector
- Sophos Central Cloud Collector
- Splunk Cloud Collector
- STIX/TAXII Cloud Collector
- Symantec Endpoint Security Cloud Collector
- Tenable Cloud Collector
- Trend Vision One Cloud Collector
- Trellix Endpoint Security Cloud Collector
- Vectra Cloud Collector
- Zoom Cloud Collector
- Zscaler ZIA Cloud Collector
- Webhook Cloud Collectors
- Wiz Issues Cloud Collector
- Wiz API Cloud Collector
- Troubleshooting Cloud Collectors
Prerequisites to Configure the Box Cloud Collector
Before you configure the Box Cloud Collector you must complete the following prerequisites:
Ensure that the https://*.box.com service is open for communication with the New-Scale Security Operations Platform.
Enable two-factor authentication.
Obtain the JWT JSON file by creating a Box Platform App.
(Optional) Enable the Box shield events to collect data.
Enable Two-factor Authentication
Before you configure the Box cloud collector, you must enable two-factor authentication for the Box account. To enable two-factor authentication:
Log in to the Box account by accessing https://app.box.com/account.
Navigate to Account Settings > Account > Authentication.
Select Require 2-step verification to protect your account. For more information, see the Box Documentation.
Enter a mobile phone number to enable the two-factor authentication and click Continue.
Obtain the JSON file by Creating a Box Platform App
Box APIs are authenticated via application keys using JSON Web Tokens (JWT) to allow server-to-server authentication. JWT uses a public key pair to verify the application's permissions. You must create a Box platform app to obtain the JSON file to use while configuring the Box cloud collector.
To create a Box app:
Log in to the Box developer console.
On the My Platform Apps page, click Create Platform App.
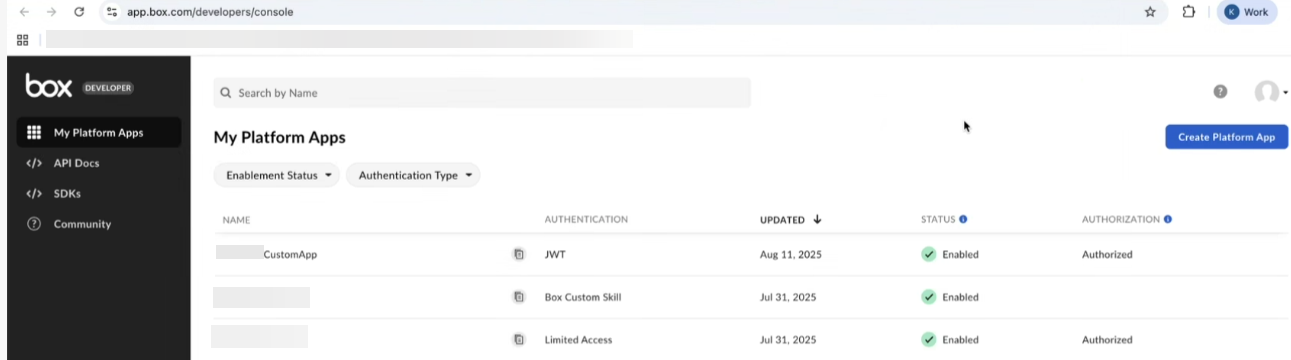
Select the app type Custom apps.
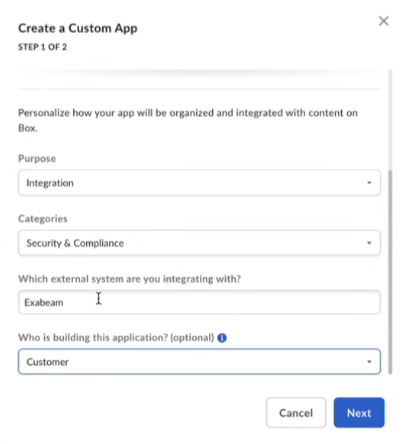
On the Create a Custom App page, enter the details such as app name, description, purpose for creating this app, category, and name of the external system with which you are integrating the app.
Note
Make sure to specify the app name SkyFormation Integration to prevent any additional costs associated with API calls.
In step 2, select Sever Authentication (with JWT), and click Create App.
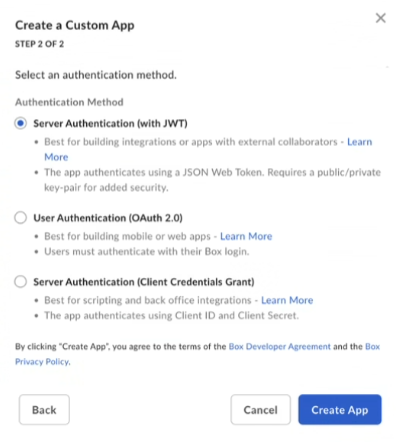
A confirmation message informs that the custom app is created.
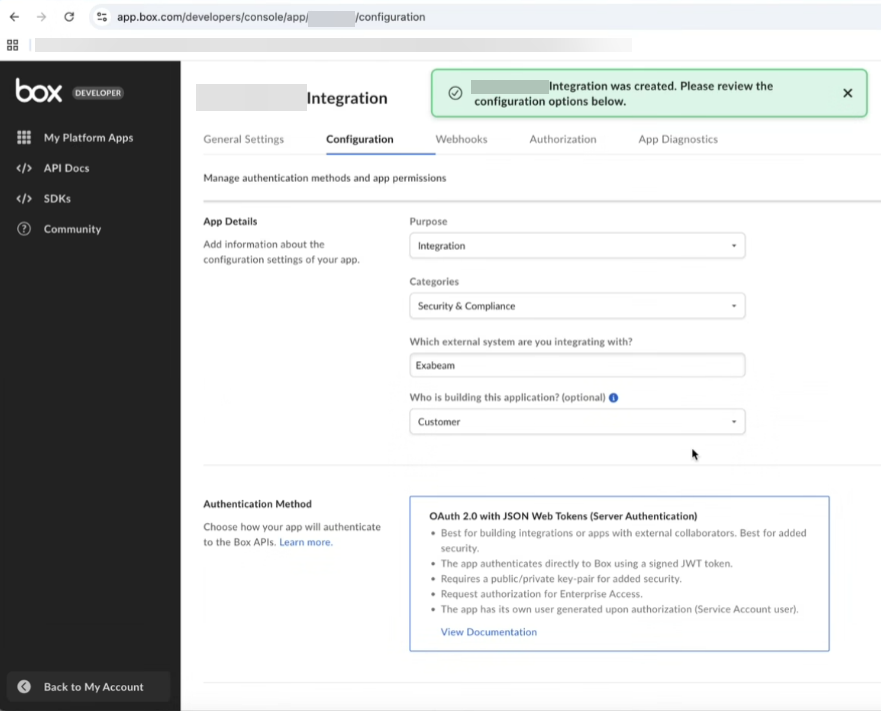
In the Configuration section, ensure that the App access level is set to App + Enterprise Access.
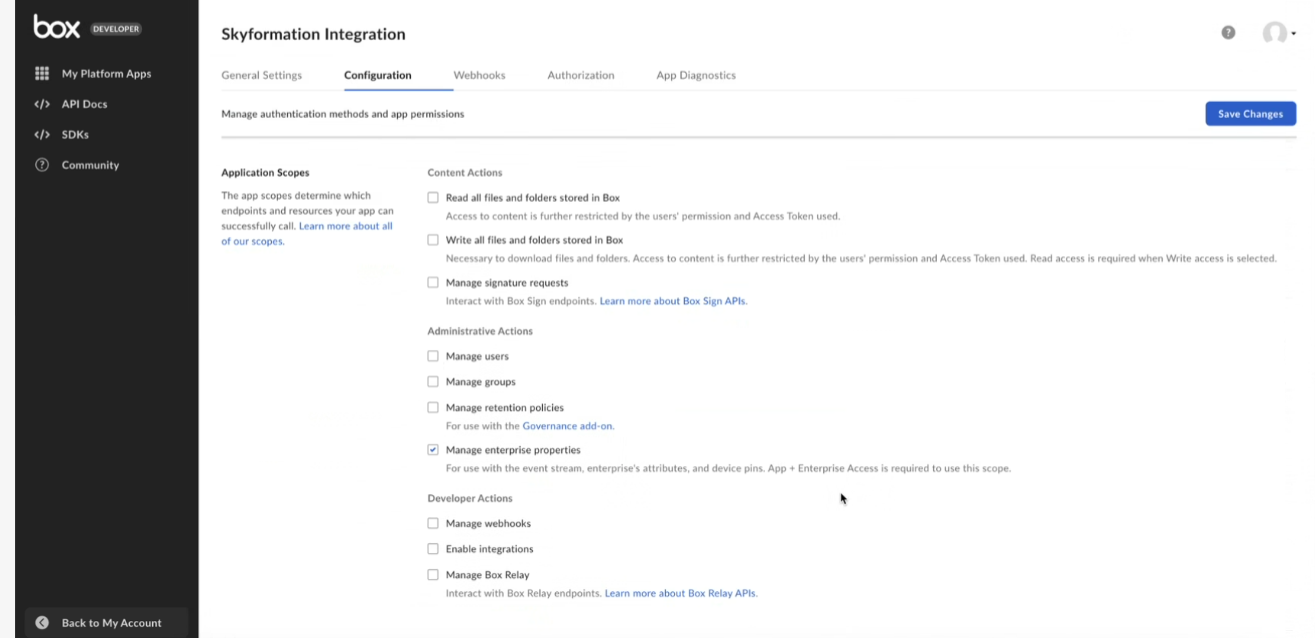
Scroll down to the Application Scopes section and to define the permissions for the application to access data select the check box for Manage enterprise properties.
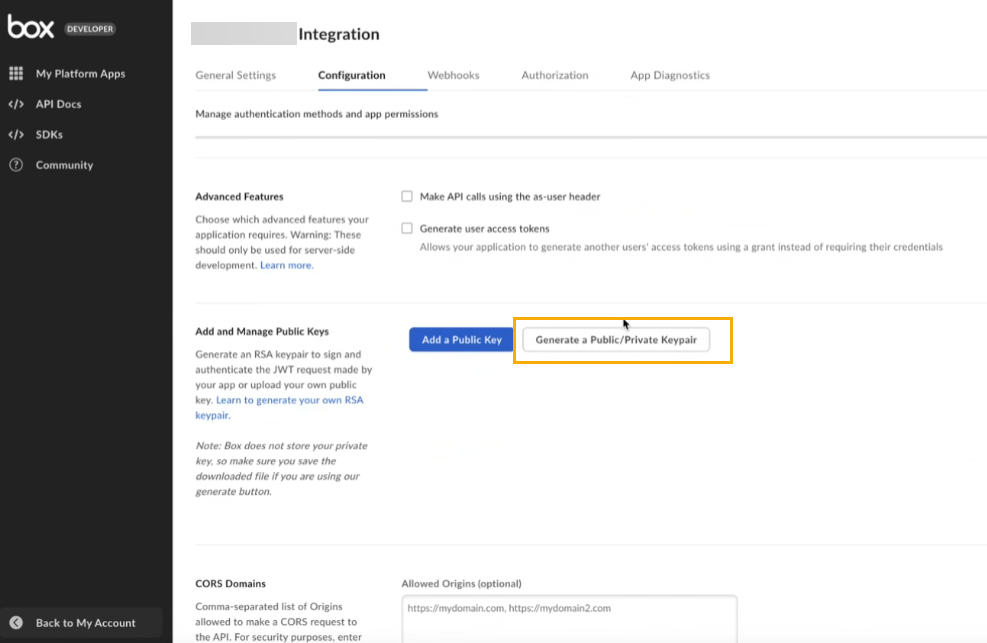
Make sure that the options in the Advanced Features section are disabled. If enabled, these options would interfere with the authentication process.
In the Add and Manage Public Keys section, click Generate a Public/Private Keypair to download a JSON configuration file.
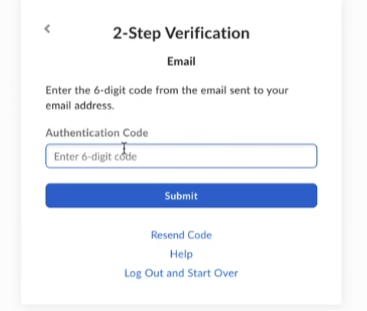
Note
Enter the authentication code that you may get via the registered email address to complete the download process.
Save the JSON configuration file and copy the data. Use this data while configuring the Box cloud collector.
Click Save Changes.
In the Authorization tab, click Review and Submit to submit the App for Authorization to the Box Administrator and thereafter get the app authorized by the Box Administrator.
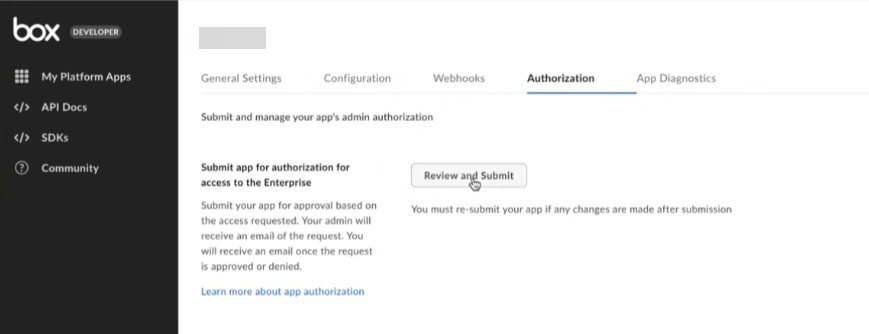
The request is submitted for Box administrator's approval. To avoid test connection failure, ensure that you create a request to authorize the app, and get the request approved by the Box administrator. The Box administrator can authorize the app by accessing the Box administrator account on https://app.box.com/account, and then navigating to Admin Console > Integrations > Platform Apps Manager.

Check that the Box Account Admin user has granted the permissions that you requested for the Box Platform App.
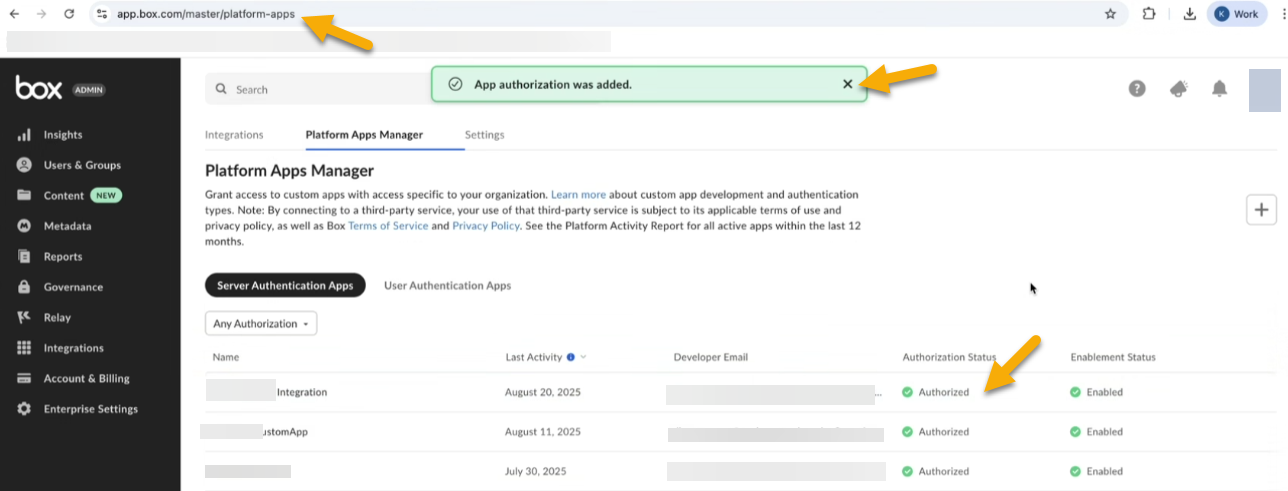
The Box admin user must have the Account Admin role to grant the requested access permissions. To ensure that the user has the Account Admin role, log in to the Box account by accessing https://app.box.com/account, and navigate to the Account Details section and check the username in the Admin Contact section.
Enable Box Shield Events
The Box Shield alert events provide security incident alerts such as suspicious locations, suspicious sessions, anomalous download, and malicious content. The shield alert events are produced within the enterprise event stream.
The Cloud Collector for Box consumes the enterprise event stream to collect the data from Box Shield notifications. You can configure the Box account to include shield alerts if your Box enterprise account has the Box shield events enabled. To collect this data, enable the Publish alert to Box Event Stream option while configuring the Box shield rules in the Box portal. For more information see the Box documentation.
