- Cloud Collectors Overview
- Administration
- Administrative Access
- Shareable Service Accounts
- Add Accounts for AWS Cloud Collectors
- Add Accounts for Cisco Duo Cloud Collector
- Add Accounts for Google Cloud Collectors
- Add Accounts for Microsoft Cloud Collectors
- Add Accounts for Okta Cloud Collectors
- Add Accounts for Salesforce Cloud Collectors
- Add Accounts for Splunk Cloud Collectors
- Add Accounts for Trend Micro Cloud Collectors
- Add Accounts for Wiz
- Define a Unique Site Name
- Sign Up for the Early Access Program
- Onboard Cloud Collectors
- Abnormal Security Cloud Collector
- Anomali Cloud Collector
- AWS CloudTrail Cloud Collectors
- AWS CloudWatch Cloud Collector
- AWS CloudWatch Alarms Cloud Collector
- AWS GuardDuty Cloud Collector
- AWS S3 Cloud Collector
- AWS Security Lake Cloud Collector
- AWS SQS Cloud Collector
- Azure Activity Logs Cloud Collector
- Azure Blob Storage Cloud Collector
- Azure Log Analytics Cloud Collector
- Azure Event Hub Cloud Collector
- Azure Storage Analytics Cloud Collector
- Azure Virtual Network Flow Cloud Collector
- Box Cloud Collector
- Broadcom Carbon Black Cloud Collector
- Cato Networks Cloud Collector
- Cisco Duo Cloud Collector
- Cisco Meraki Cloud Collector
- Cisco Secure Endpoint Cloud Collector
- Cisco Umbrella Cloud Collector
- Cloudflare Cloud Collector
- Cribl Cloud Collector
- CrowdStrike Cloud Collectors
- Cylance Protect (now Arctic Wolf) Cloud Collector
- DataBahn Cloud Collector
- Dropbox Cloud Collector
- GCP Cloud Logging Cloud Collector
- GCP Pub/Sub Cloud Collector
- GCP Security Command Center Cloud Collector
- Gemini Enterprise Cloud Collector
- GitHub Cloud Collector
- Gmail BigQuery Cloud Collector
- Google Workspace Cloud Collector
- LastPass Cloud Collector
- Microsoft Defender XDR (via Azure Event Hub) Cloud Collector
- Microsoft Entra ID Context Cloud Collector
- Microsoft Entra ID Logs Cloud Collector
- Microsoft 365 Exchange Admin Reports Cloud Collector
- Supported Sources from Microsoft 365 Exchange Admin Reports
- Migrate to the Microsoft 365 Exchange Admin Reports Cloud Collector
- Prerequisites to Configure the Microsoft 365 Exchange Admin Reports Cloud Collector
- Configure the Microsoft 365 Exchange Admin Reports Cloud Collector
- Troubleshooting the Microsoft 365 Exchange Admin Reports Cloud Collector
- Microsoft 365 Management Activity Cloud Collector
- Microsoft Security Alerts Cloud Collector
- Microsoft Sentinel (via Event Hub) Cloud Collector
- Mimecast Cloud Collector
- Netskope Alerts Cloud Collector
- Netskope Events Cloud Collector
- Okta Cloud Collector
- Okta Context Cloud Collector
- Palo Alto Networks Cortex Data Lake Cloud Collector
- Palo Alto Networks XDR Cloud Collector
- Progress ShareFile Cloud Collector
- Proofpoint On-Demand Cloud Collector
- Proofpoint Targeted Attack Protection Cloud Collector
- Qualys Cloud Collector
- Recorded Future Cloud Collector
- Recorded Future Context Cloud Collector
- Rest API Cloud Collector
- Salesforce Cloud Collector
- Salesforce EventLog Cloud Collector
- SentinelOne Alerts Cloud Collector
- SentinelOne Cloud Funnel Cloud Collector
- SentinelOne Threats Cloud Collector
- SentinelOne Cloud Collector
- ServiceNow Cloud Collector
- Slack Cloud Collector
- Snowflake Cloud Collector
- Sophos Central Cloud Collector
- Splunk Cloud Collector
- STIX/TAXII Cloud Collector
- Symantec Endpoint Security Cloud Collector
- Tenable Cloud Collector
- Trend Vision One Cloud Collector
- Trellix Endpoint Security Cloud Collector
- Vectra Cloud Collector
- Zoom Cloud Collector
- Zscaler ZIA Cloud Collector
- Webhook Cloud Collectors
- Wiz Issues Cloud Collector
- Wiz API Cloud Collector
- Troubleshooting Cloud Collectors
View Cloud Collector Error Notifications
The New-Scale Security Operations Platform provides you with error notifications and notifications for time sensitive security and health issues for Cloud collectors via user interface to monitor the status and health of your collectors. For more information see Notifications.
The New-Scale Security Operations Platform notifications service provides:
Precise error messages with metadata for consistent, clear, and actionable notifications
Configurability to minimize notification noise
Filters for improved notification management
Inbox for enhanced notification review
Additional external messaging channels
View Notifications for Cloud Collectors
The New-Scale Security Operations Platform notifications service includes error notifications about Cloud Collectors service. To view the collector notifications, click the notifications icon ( ).
).
The Cloud Collector notifications are generated when an error occurs in log ingestion or volume for any of the collector instance.
To view notifications about cloud collector errors:
Log in to the New-Scale Security Operations Platform and click the Notifications icon (
 ) in the upper right corner.
) in the upper right corner.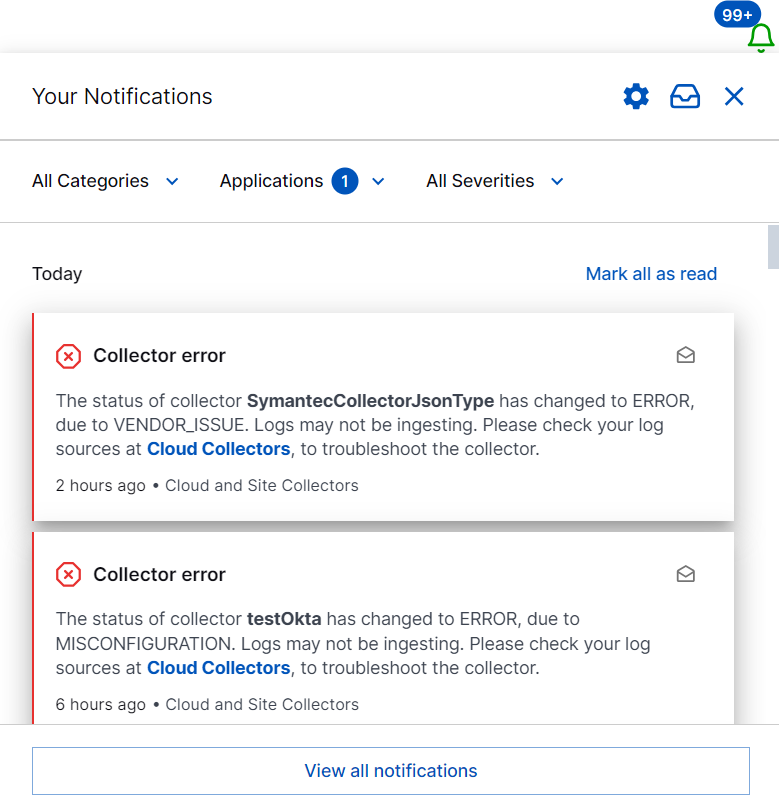
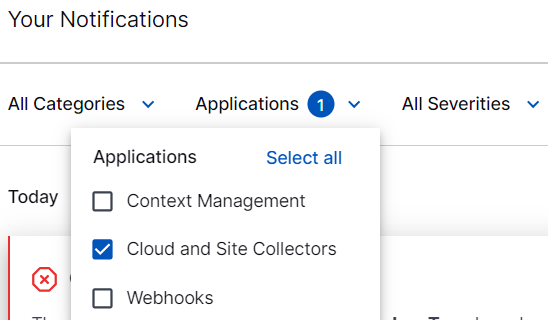
Click the Applications filter and select Cloud and Site Collectors.
The notifications relevant for Cloud and Site Collectors are listed.
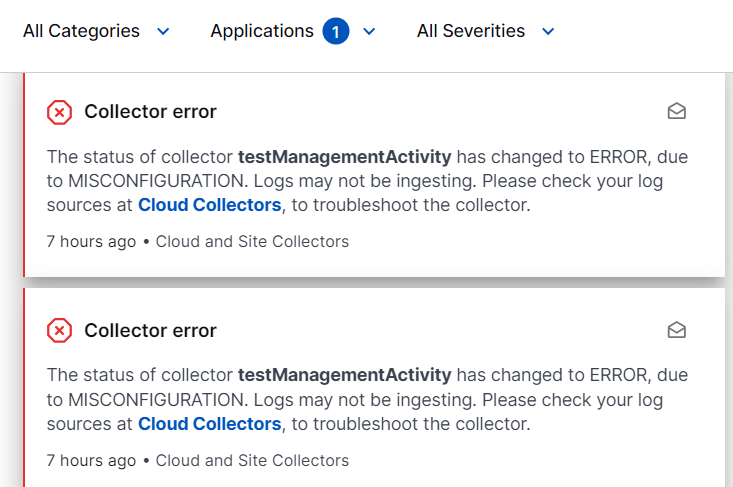
To view error details, click the Cloud Collectors link in the error notification.
The specific cloud collector instance displays error details.
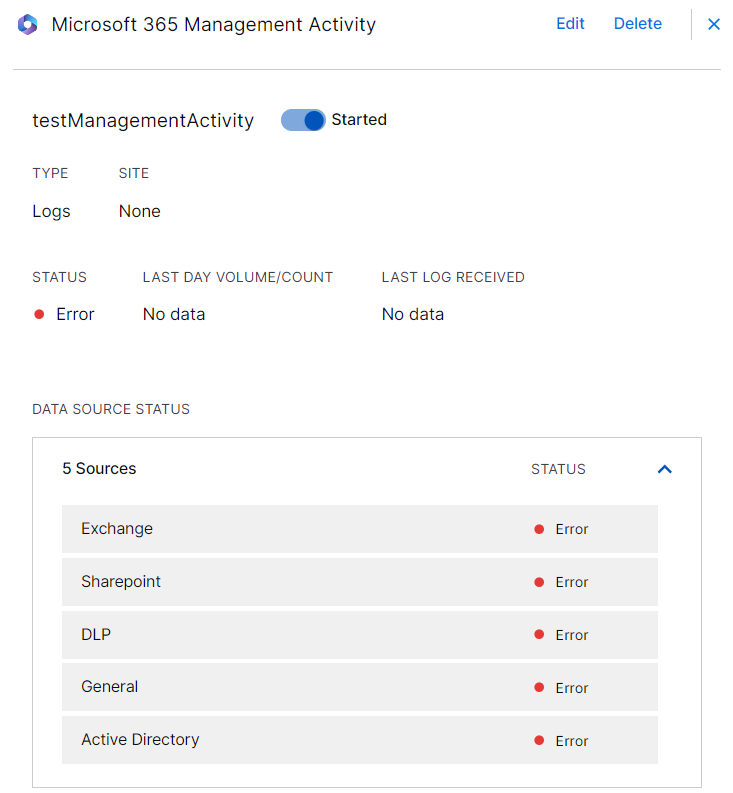
Scroll down to view full details of the error and the recommended action to resolve the error.
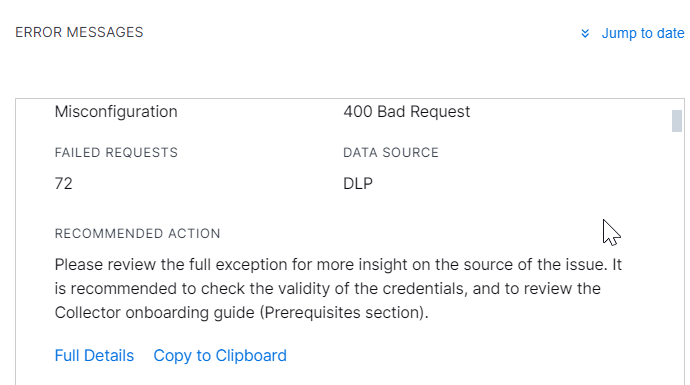
By default, these notifications are received in the application, but you can also choose to receive them via email. For more information, see Manage Notification Preferences.
To configure group notification delivery via Teams, Slack, or web hooks, see Manage Global Notification Preferences.
The following table displays the available collector notification types.
Notification Type
Description
Collector Error
Indicates cloud collector specific errors.
Indicates that log volume has decreased.
Indicates that there is an increase in log volume.
Filter Notifications
To view notifications based on categories, applications, and severities for cloud collectors, apply relevant filters.
Categories
Applications
Severities
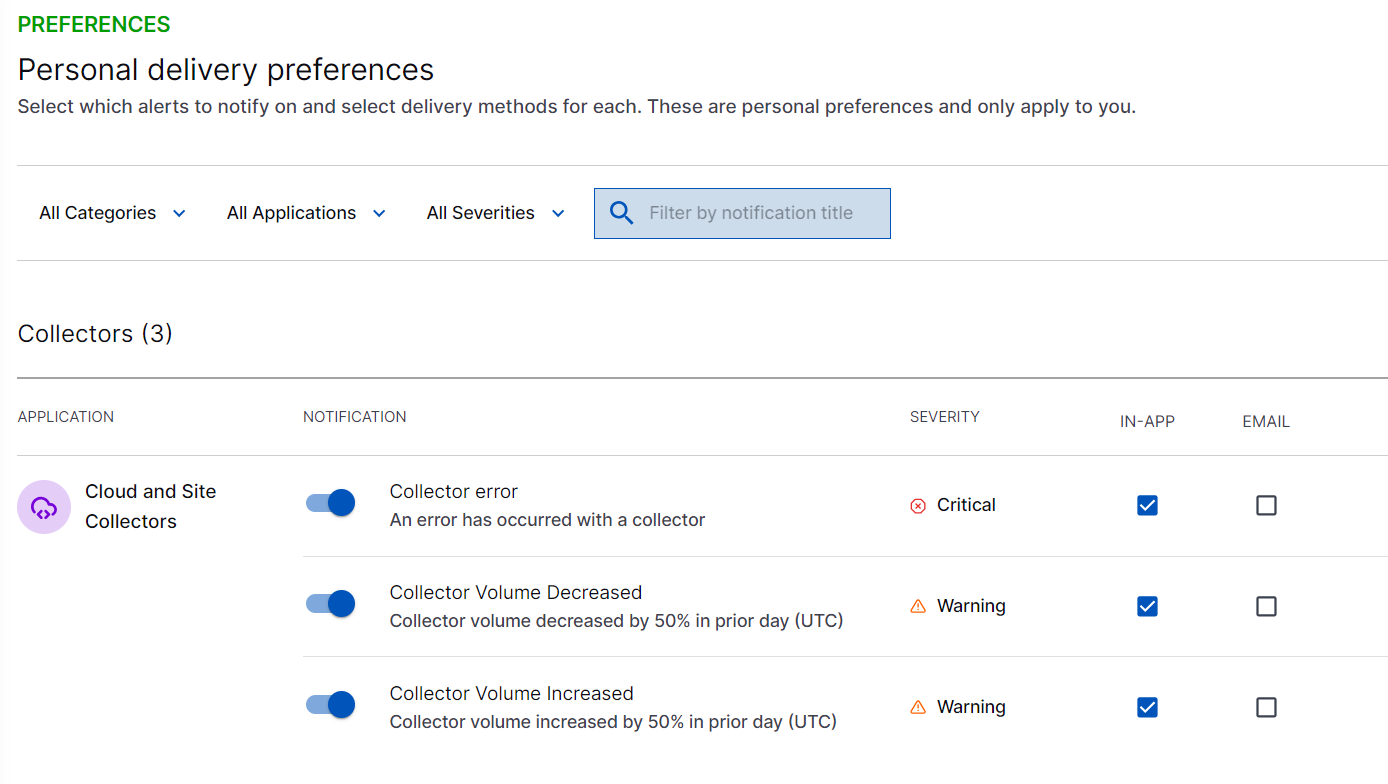
Manage Preferences for Notifications
You can manage preferences to view notifications. Based on what notifications you want to see in the Your Notifications pane, you can turn on or turn off the notification types such as notifications for collector error or notifications for collector volume. To view the Personal delivery preferences page and set preferences for notifications on collector errors, click the Settings icon ( ).
).
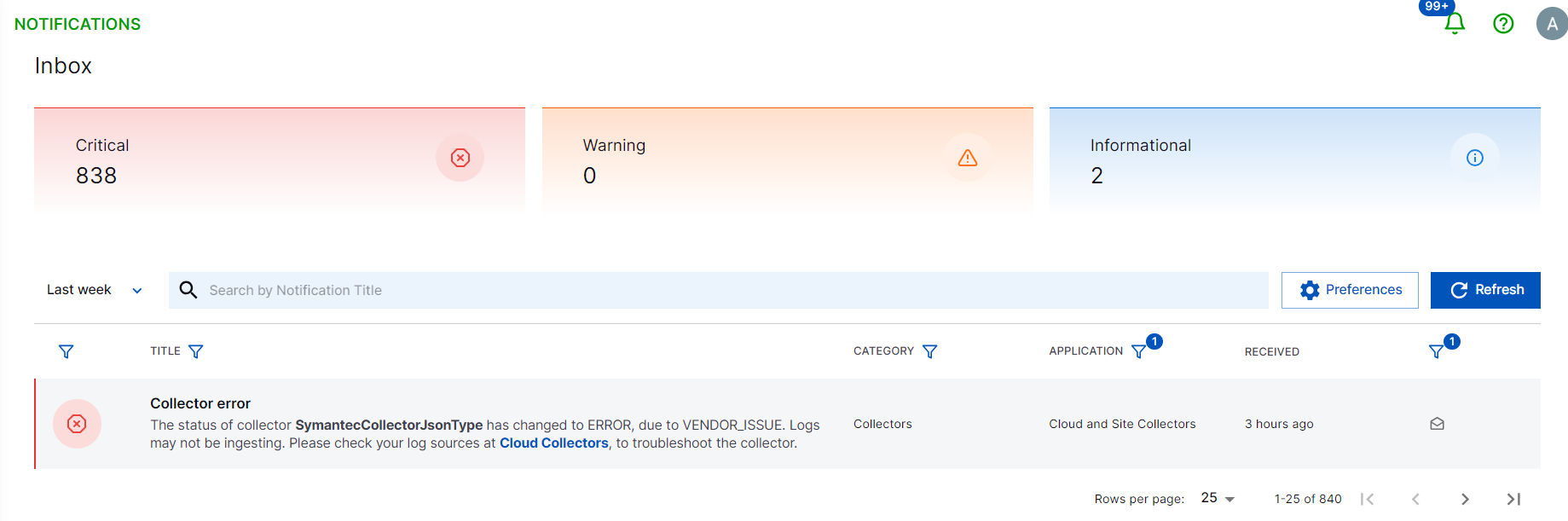
View Inbox for Notification Review
To view the cloud collector notifications received over the last 90 days, click the Inbox icon ( ). You can view number of notifications classified as Critical, Warning, and Informational. You can apply various filters to the notification based on your preferences and requirement. You can also search for a particular notification. For more information see View Inbox.
). You can view number of notifications classified as Critical, Warning, and Informational. You can apply various filters to the notification based on your preferences and requirement. You can also search for a particular notification. For more information see View Inbox.