- Cloud Collectors Overview
- Administration
- Administrative Access
- Shareable Service Accounts
- Add Accounts for AWS Cloud Collectors
- Add Accounts for Cisco Duo Cloud Collector
- Add Accounts for Google Cloud Collectors
- Add Accounts for Microsoft Cloud Collectors
- Add Accounts for Okta Cloud Collectors
- Add Accounts for Salesforce Cloud Collectors
- Add Accounts for Splunk Cloud Collectors
- Add Accounts for Trend Micro Cloud Collectors
- Add Accounts for Wiz
- Define a Unique Site Name
- Sign Up for the Early Access Program
- Onboard Cloud Collectors
- Abnormal Security Cloud Collector
- Anomali Cloud Collector
- AWS CloudTrail Cloud Collectors
- AWS CloudWatch Cloud Collector
- AWS CloudWatch Alarms Cloud Collector
- AWS GuardDuty Cloud Collector
- AWS S3 Cloud Collector
- AWS Security Lake Cloud Collector
- AWS SQS Cloud Collector
- Azure Activity Logs Cloud Collector
- Azure Blob Storage Cloud Collector
- Azure Log Analytics Cloud Collector
- Azure Event Hub Cloud Collector
- Azure Storage Analytics Cloud Collector
- Azure Virtual Network Flow Cloud Collector
- Box Cloud Collector
- Broadcom Carbon Black Cloud Collector
- Cato Networks Cloud Collector
- ChatGPT Enterprise Cloud Collector
- Cisco Duo Cloud Collector
- Cisco Meraki Cloud Collector
- Cisco Secure Endpoint Cloud Collector
- Cisco Umbrella Cloud Collector
- Cloudflare Cloud Collector
- Cribl Cloud Collector
- CrowdStrike Cloud Collectors
- Cylance Protect (now Arctic Wolf) Cloud Collector
- DataBahn Cloud Collector
- Dropbox Cloud Collector
- GCP Cloud Logging Cloud Collector
- GCP Pub/Sub Cloud Collector
- GCP Security Command Center Cloud Collector
- Gemini Enterprise Cloud Collector
- GitHub Cloud Collector
- Gmail BigQuery Cloud Collector
- Google Workspace Cloud Collector
- LastPass Cloud Collector
- Microsoft Defender XDR (via Azure Event Hub) Cloud Collector
- Microsoft Entra ID Context Cloud Collector
- Microsoft Entra ID Logs Cloud Collector
- Microsoft 365 Exchange Admin Reports Cloud Collector
- Supported Sources from Microsoft 365 Exchange Admin Reports
- Migrate to the Microsoft 365 Exchange Admin Reports Cloud Collector
- Prerequisites to Configure the Microsoft 365 Exchange Admin Reports Cloud Collector
- Configure the Microsoft 365 Exchange Admin Reports Cloud Collector
- Troubleshooting the Microsoft 365 Exchange Admin Reports Cloud Collector
- Microsoft 365 Management Activity Cloud Collector
- Microsoft Security Alerts Cloud Collector
- Microsoft Sentinel (via Event Hub) Cloud Collector
- Mimecast Cloud Collector
- Mimecast Incydr Cloud Collector
- Netskope Alerts Cloud Collector
- Netskope Events Cloud Collector
- Okta Cloud Collector
- Okta Context Cloud Collector
- Palo Alto Networks Cortex Data Lake Cloud Collector
- Palo Alto Networks XDR Cloud Collector
- Progress ShareFile Cloud Collector
- Proofpoint On-Demand Cloud Collector
- Proofpoint Targeted Attack Protection Cloud Collector
- Qualys Cloud Collector
- Recorded Future Cloud Collector
- Recorded Future Context Cloud Collector
- Rest API Cloud Collector
- Salesforce Cloud Collector
- Salesforce EventLog Cloud Collector
- SentinelOne Alerts Cloud Collector
- SentinelOne Cloud Funnel Cloud Collector
- SentinelOne Threats Cloud Collector
- SentinelOne Cloud Collector
- ServiceNow Cloud Collector
- Slack Cloud Collector
- Snowflake Cloud Collector
- Sophos Central Cloud Collector
- Splunk Cloud Collector
- STIX/TAXII Cloud Collector
- Symantec Endpoint Security Cloud Collector
- Tenable Cloud Collector
- Trend Vision One Cloud Collector
- Trellix Endpoint Security Cloud Collector
- Vectra Cloud Collector
- Zoom Cloud Collector
- Zscaler ZIA Cloud Collector
- Webhook Cloud Collectors
- Wiz Issues Cloud Collector
- Wiz API Cloud Collector
- Troubleshooting Cloud Collectors
Prerequisites to Configure the Cisco Umbrella Cloud Collector
Complete the following prerequisites to configure the Cisco Umbrella Cloud Collector:
Obtain the Cisco managed S3 bucket data including the access key, secret key, data path, and the S3 bucket name, if you want to use S3 bucket managed by Cisco.
Obtain the company managed S3 bucket data, if you want to use S3 bucket managed by your organization.
Add Accounts for AWS Cloud Collectors to use the same account information across multiple Cisco Umbrella cloud collectors.
Get full administrative access to Cisco Umbrella.
Obtain the Cisco Managed S3 Bucket Data
Cisco Umbrella APIs are authenticated via application keys. You must obtain the Cisco managed S3 bucket data that contains access key, secret key, data path, and S3 bucket name to use while configuring the Cisco Umbrella Cloud Collector.
To obtain Cisco managed S3 bucket data that contains access key, secret key, and client ID:
Log in to the Cisco Umbrella console by accessing https://login.umbrella.com/ as an administrator.
Navigate to Admin > Log Management.
Click Use a Cisco-managed Amazon S3 bucket.
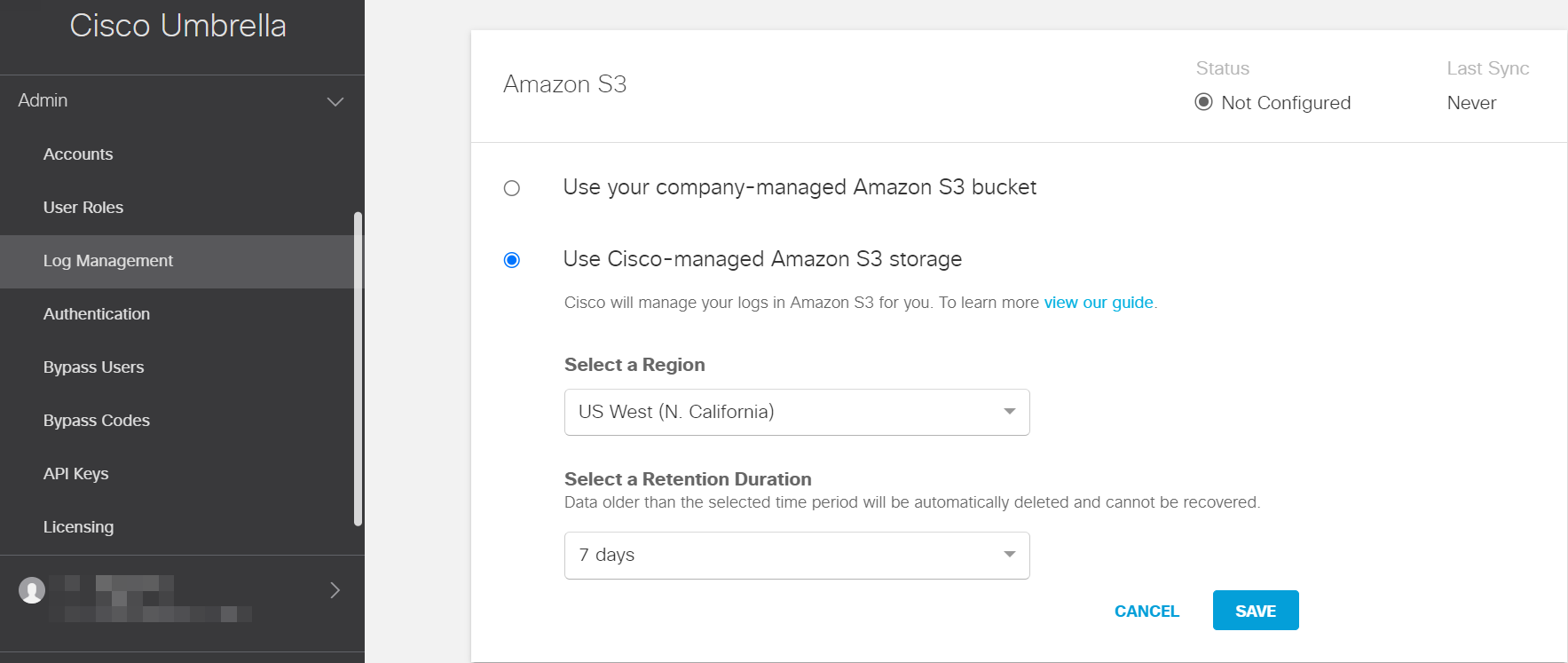
Select a region that is closer to you. The regional endpoints are required to reduce latency while downloading logs to your servers.
Select a time-period from the Select a Retention Duration list and click Save. After the selected time-period, all the data is purged and cannot be retrieved.
In the confirmation box that displays selected region and retention duration, click Continue to confirm the settings.
Cisco sends an activation notification. When the activation is complete, the Amazon S3 Summary page displays the data path, an access key, and a secret key.
Record the values for the data path, access key, and secret key. The values appear only once, if you lose the key values, you must regenerate the values.

After noting the values, select Got it, and click Continue. For more information, see the Cisco Umbrella documentation. The data path value contains S3 bucket name and data path. Note the values to use them while configuring the Cisco Umbrella Cloud Collector on the New-Scale Security Operations Platform.
Proceed to Configure the Cisco Umbrella Cloud Collector.
Obtain the Company Managed S3 Bucket Data
Create a bucket policy to grant other AWS accounts or IAM users access permissions for the bucket and the objects in the bucket. For more information see Amazon S3 bucket policies.
To create or edit the bucket policy:
In the AWS management console, edit the bucket policy to ensure that the bucket accepts uploads from Cisco Umbrella by replacing bucketname with the S3 bucket name that you specify in the JSON file using the bucket policy text editor. For more information see the Cisco Umbrella Documentation and the AWS bucket policy guide.
In the Cisco Umbrella console, navigate to Admin > Log Management.
Click Use your company-managed Amazon S3 bucket.

Enter the Amazon S3 bucket name that you specified in the JSON file.
Click Verify.
Cisco Umbrella verifies and connects to the bucket and saves a README_FROM_UMBRELLA.txt file to the bucket.
Copy the token from the README_FROM_UMBRELLA.txt file that Cisco Umbrella saved to your bucket.
Paste the token in the Token Number field.
Click Save.
Proceed to Configure the Cisco Umbrella Cloud Collector.
