- Cloud Collectors Overview
- Administration
- Administrative Access
- Shareable Service Accounts
- Add Accounts for AWS Cloud Collectors
- Add Accounts for Cisco Duo Cloud Collector
- Add Accounts for Google Cloud Collectors
- Add Accounts for Microsoft Cloud Collectors
- Add Accounts for Okta Cloud Collectors
- Add Accounts for Salesforce Cloud Collectors
- Add Accounts for Splunk Cloud Collectors
- Add Accounts for Trend Micro Cloud Collectors
- Add Accounts for Wiz
- Define a Unique Site Name
- Sign Up for the Early Access Program
- Supported Cloud Collectors
- Onboard Cloud Collectors
- Abnormal Security Cloud Collector
- Anomali Cloud Collector
- AWS CloudTrail Cloud Collectors
- AWS CloudWatch Cloud Collector
- AWS CloudWatch Alarms Cloud Collector
- AWS GuardDuty Cloud Collector
- AWS S3 Cloud Collector
- AWS Security Lake Cloud Collector
- AWS SQS Cloud Collector
- Azure Activity Logs Cloud Collector
- Azure Blob Storage Cloud Collector
- Azure Log Analytics Cloud Collector
- Azure Event Hub Cloud Collector
- Azure Storage Analytics Cloud Collector
- Azure Virtual Network Flow Cloud Collector
- Box Cloud Collector
- Broadcom Carbon Black Cloud Collector
- Cato Networks Cloud Collector
- ChatGPT Enterprise Cloud Collector
- Cisco Duo Cloud Collector
- Cisco Meraki Cloud Collector
- Cisco Secure Endpoint Cloud Collector
- Cisco Umbrella Cloud Collector
- Cloudflare Cloud Collector
- Cribl Cloud Collector
- CrowdStrike Cloud Collectors
- Cylance Protect (now Arctic Wolf) Cloud Collector
- DataBahn Cloud Collector
- Dropbox Cloud Collector
- GCP Cloud Logging Cloud Collector
- GCP Pub/Sub Cloud Collector
- GCP Security Command Center Cloud Collector
- Gemini Enterprise Cloud Collector
- GitHub Cloud Collector
- Gmail BigQuery Cloud Collector
- Google Workspace Cloud Collector
- LastPass Cloud Collector
- Microsoft Defender XDR (via Azure Event Hub) Cloud Collector
- Microsoft Entra ID Context Cloud Collector
- Microsoft Entra ID Logs Cloud Collector
- Microsoft 365 Exchange Admin Reports Cloud Collector
- Supported Sources from Microsoft 365 Exchange Admin Reports
- Migrate to the Microsoft 365 Exchange Admin Reports Cloud Collector
- Prerequisites to Configure the Microsoft 365 Exchange Admin Reports Cloud Collector
- Configure the Microsoft 365 Exchange Admin Reports Cloud Collector
- Troubleshooting the Microsoft 365 Exchange Admin Reports Cloud Collector
- Microsoft 365 Management Activity Cloud Collector
- Microsoft Security Alerts Cloud Collector
- Microsoft Sentinel (via Event Hub) Cloud Collector
- Mimecast Cloud Collector
- Mimecast Incydr Cloud Collector
- Netskope Alerts Cloud Collector
- Netskope Events Cloud Collector
- Okta Cloud Collector
- Okta Context Cloud Collector
- Palo Alto Networks Cortex Data Lake Cloud Collector
- Palo Alto Networks XDR Cloud Collector
- Progress ShareFile Cloud Collector
- Proofpoint On-Demand Cloud Collector
- Proofpoint Targeted Attack Protection Cloud Collector
- Qualys Cloud Collector
- Recorded Future Cloud Collector
- Recorded Future Context Cloud Collector
- Rest API Cloud Collector
- S2W Threat Intelligence Cloud Collector
- Salesforce Cloud Collector
- Salesforce EventLog Cloud Collector
- SentinelOne Alerts Cloud Collector
- SentinelOne Cloud Funnel Cloud Collector
- SentinelOne Threats Cloud Collector
- SentinelOne Cloud Collector
- ServiceNow Cloud Collector
- Slack Cloud Collector
- Snowflake Cloud Collector
- Sophos Central Cloud Collector
- Splunk Cloud Collector
- STIX/TAXII Cloud Collector
- Symantec Endpoint Security Cloud Collector
- Tenable Cloud Collector
- Trend Vision One Cloud Collector
- Trellix Endpoint Security Cloud Collector
- Vectra Cloud Collector
- Zoom Cloud Collector
- Zscaler ZIA Cloud Collector
- Webhook Cloud Collectors
- Wiz Issues Cloud Collector
- Wiz API Cloud Collector
- Troubleshooting Cloud Collectors
Prerequisites to Configure the Microsoft Sentinel (via Event Hub) Cloud Collector
Before you configure the Microsoft Sentinel (via Event Hub) Cloud Collector you must complete the following prerequisites:
Configure Microsoft Sentinel and Log Analytics workspace in Azure portal.
Obtain the consumer group name to be entered while configuring the Cloud Collector.
Obtain the connection string to be entered while configuring the Cloud Collector.
(Optional) Configure your Event Hub setup for enabling sufficient egress. Consider referring to the tip in this section.
Add supported data connectors to Microsoft Sentinel.
Ensure that you have Azure subscription with standard, or premium, or dedicated tier of Azure Event Hubs. Cloud Collectors do not support the Basic tier of Azure Event Hubs for event ingestion. For more information about various tiers of Azure Event Hubs, see Compare Azure Event Hubs tiers in the Microsoft documentation.
Note
Parsing of data collected from Microsoft Sentinel is only supported for New Scale Search and Advanced Analytics i63 or later.
Configure Microsoft Sentinel and Log Analytics Workspace
To ingest logs from Microsoft Sentinel via Azure Event Hub, you must configure Microsoft Sentinel. Add Microsoft Sentinel to an existing workspace or create a new Log Analytics workspace. For more information, see Microsoft Documentation.
Obtain the Consumer Group Name and Connection String
Before configuring the Microsoft Sentinel (via Event Hub) Cloud Collector, use the following steps to obtain the Consumer Group Name and Connection String for your Event Hub endpoint.
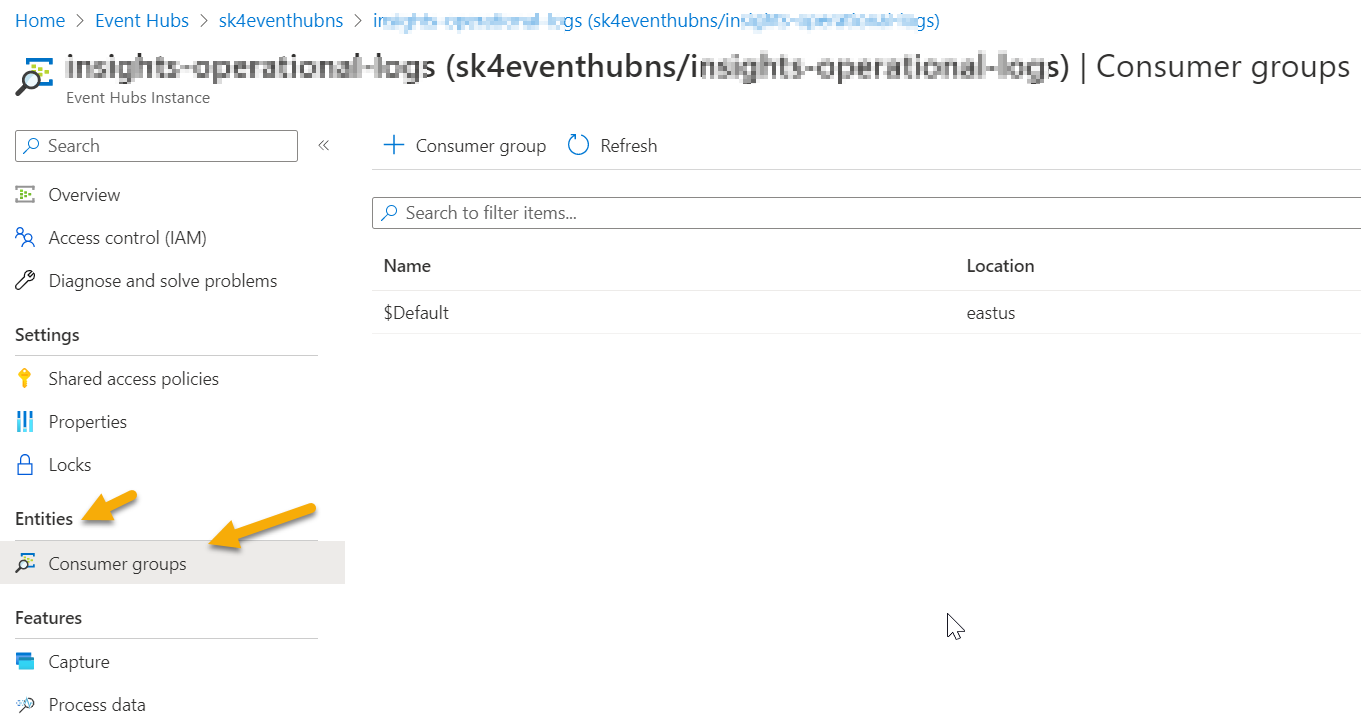
To obtain the name of the consumer group of the Event Hub, perform the following steps.
On the Azure portal, navigate to the Event Hubs namespace in which the Event Hub with the data you want to retrieve resides.
Select the EventHub where your data to be retrieved resides.
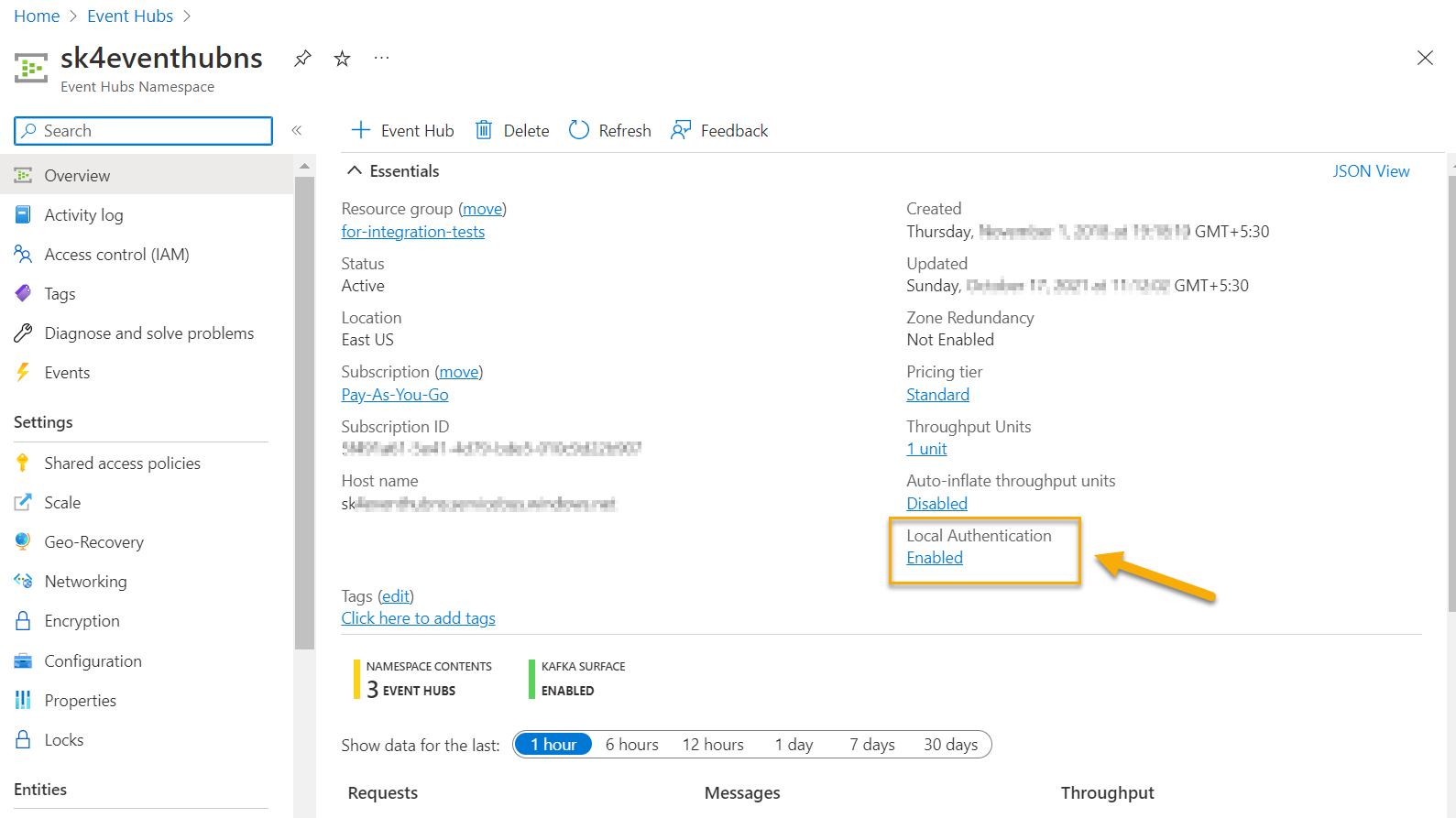
Note
If connection errors occur after the Cloud Collector configuration, enable local authentication for a given Event Hubs namespace.
Navigate to Consumer groups to note the name of the consumer group.
Note
Ensure that you create and use a unique consumer group for each EventHub that you configure. If you use the same consumer group for two cloud collector instances, it may result in event loss or ingestion issues.
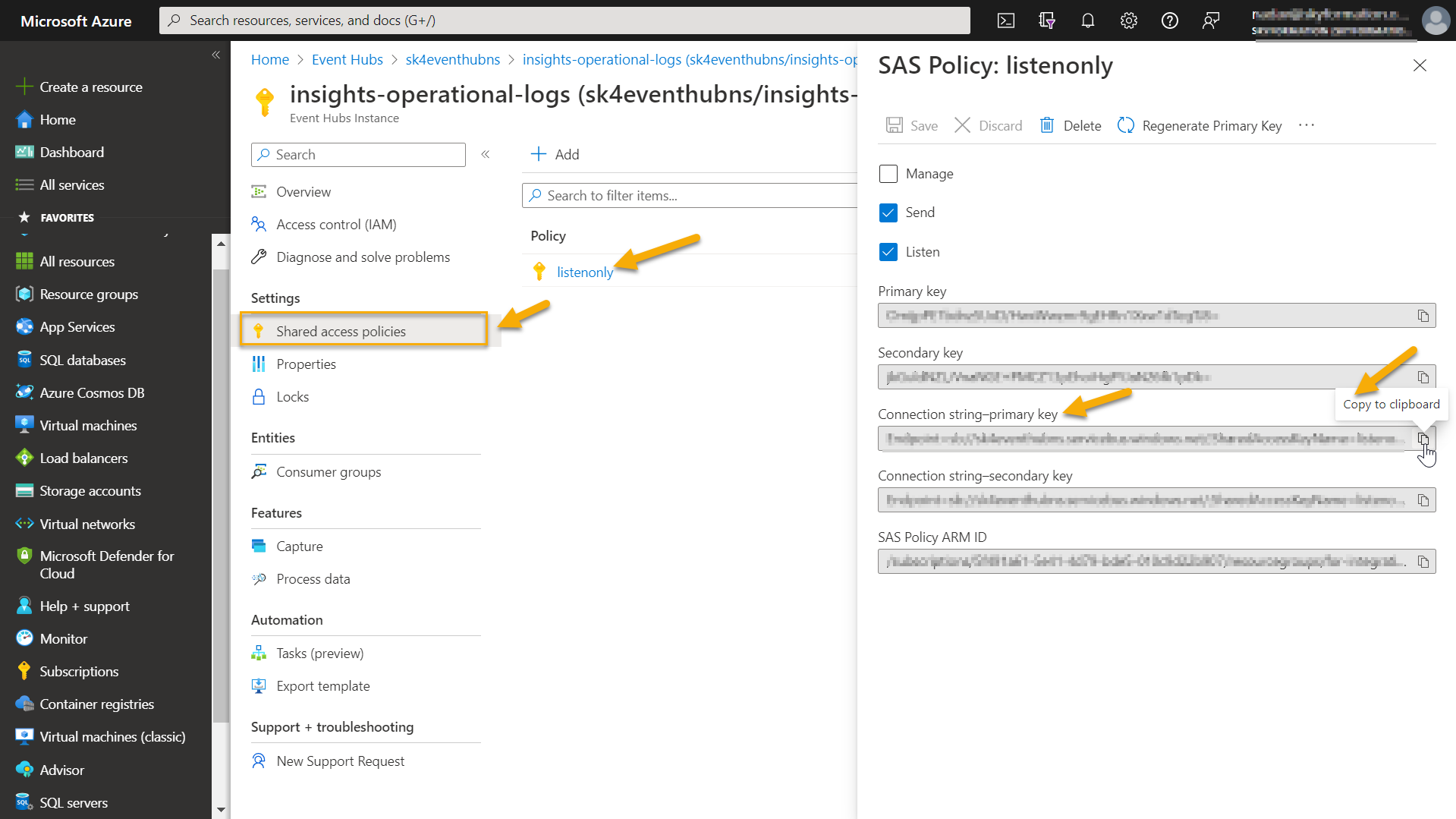
Create a SAS policy with listen-only permissions for Exabeam:
In Event Hub, navigate to Shared access policies.
Click + Add to add a new Policy on the Add SAS Policy page and enable the Listen or Manage permission based on your requirement.
Provide a descriptive name for the token which is listen-only, then click Create.
After you see the confirmation message (for example Creating SAS Policy successful), access the policy you just created and note the following.
SAS policy name
Primary key value
Note
The Connection string primary key acts as a connection string for the Azure Event Hub Cloud Collector.
Proceed to configure the Microsoft Sentinel (via Event Hub) Cloud Collector.
Tip
To configure your Event Hub setup for enabling sufficient egress, refer to the following tips.
Examine the incoming number of bytes per second, by navigating to the Event Hub page on the Azure portal.
Set up the Event Hub with a good throughput capacity. The egress and ingress capacity of Event Hubs is measured by throughput units (TU). Ensure that your Event Hub provides 1 Throughput Unit (TU) per 2MB/sec egress and 1MB/sec ingress capacity.
Ensure that your Event Hub has 32 partitions and at least 1 TU per partition.
If you notice that your workload requirement exceeds the maximum value recommended for Event Hub Premium which is 32 partitions and 40 TU, you need to migrate to a Dedicated Event Hub Cluster.
Consider using the Auto-inflate throughput feature. You can enable Auto-inflate on the Event Hub namespace to automatically increase the number of TUs based on the load. For more information about throughput units, limits, and associated billing, see Event Hubs FAQs and Azure Event Hubs quotas and limits.
Add Supported Data Connectors
To start ingesting logs into Microsoft Sentinel, add data connectors by following instructions mentioned in the Microsoft Sentinel data connectors topic in the Microsoft documentation.
Create a data export rule that defines the destination and tables for which data is exported. Microsoft Sentinel supports specific tables to be exported. See the list of Supported tables in the Microsoft documentation.
To forward the ingested logs from Microsoft Sentinel to Event Hub, navigate to the Log Analytics workspace that you created and click Data export. Create a rule by clicking New export rule in which you add Event Hub details.
