- Cloud Collectors Overview
- Administration
- Administrative Access
- Shareable Service Accounts
- Add Accounts for AWS Cloud Collectors
- Add Accounts for Cisco Duo Cloud Collector
- Add Accounts for Google Cloud Collectors
- Add Accounts for Microsoft Cloud Collectors
- Add Accounts for Okta Cloud Collectors
- Add Accounts for Salesforce Cloud Collectors
- Add Accounts for Splunk Cloud Collectors
- Add Accounts for Trend Micro Cloud Collectors
- Add Accounts for Wiz
- Define a Unique Site Name
- Sign Up for the Early Access Program
- Supported Cloud Collectors
- Onboard Cloud Collectors
- Abnormal Security Cloud Collector
- Anomali Cloud Collector
- AWS CloudTrail Cloud Collectors
- AWS CloudWatch Cloud Collector
- AWS CloudWatch Alarms Cloud Collector
- AWS GuardDuty Cloud Collector
- AWS S3 Cloud Collector
- AWS Security Lake Cloud Collector
- AWS SQS Cloud Collector
- Azure Activity Logs Cloud Collector
- Azure Blob Storage Cloud Collector
- Azure Log Analytics Cloud Collector
- Azure Event Hub Cloud Collector
- Azure Storage Analytics Cloud Collector
- Azure Virtual Network Flow Cloud Collector
- Box Cloud Collector
- Broadcom Carbon Black Cloud Collector
- Cato Networks Cloud Collector
- ChatGPT Enterprise Cloud Collector
- Cisco Duo Cloud Collector
- Cisco Meraki Cloud Collector
- Cisco Secure Endpoint Cloud Collector
- Cisco Umbrella Cloud Collector
- Cloudflare Cloud Collector
- Cribl Cloud Collector
- CrowdStrike Cloud Collectors
- Cylance Protect (now Arctic Wolf) Cloud Collector
- DataBahn Cloud Collector
- Dropbox Cloud Collector
- GCP Cloud Logging Cloud Collector
- GCP Pub/Sub Cloud Collector
- GCP Security Command Center Cloud Collector
- Gemini Enterprise Cloud Collector
- GitHub Cloud Collector
- Gmail BigQuery Cloud Collector
- Google Workspace Cloud Collector
- LastPass Cloud Collector
- Microsoft Defender XDR (via Azure Event Hub) Cloud Collector
- Microsoft Entra ID Context Cloud Collector
- Microsoft Entra ID Logs Cloud Collector
- Microsoft 365 Exchange Admin Reports Cloud Collector
- Supported Sources from Microsoft 365 Exchange Admin Reports
- Migrate to the Microsoft 365 Exchange Admin Reports Cloud Collector
- Prerequisites to Configure the Microsoft 365 Exchange Admin Reports Cloud Collector
- Configure the Microsoft 365 Exchange Admin Reports Cloud Collector
- Troubleshooting the Microsoft 365 Exchange Admin Reports Cloud Collector
- Microsoft 365 Management Activity Cloud Collector
- Microsoft Security Alerts Cloud Collector
- Microsoft Sentinel (via Event Hub) Cloud Collector
- Mimecast Cloud Collector
- Mimecast Incydr Cloud Collector
- Netskope Alerts Cloud Collector
- Netskope Events Cloud Collector
- Okta Cloud Collector
- Okta Context Cloud Collector
- Palo Alto Networks Cortex Data Lake Cloud Collector
- Palo Alto Networks XDR Cloud Collector
- Progress ShareFile Cloud Collector
- Proofpoint On-Demand Cloud Collector
- Proofpoint Targeted Attack Protection Cloud Collector
- Qualys Cloud Collector
- Recorded Future Cloud Collector
- Recorded Future Context Cloud Collector
- Rest API Cloud Collector
- S2W Threat Intelligence Cloud Collector
- Salesforce Cloud Collector
- Salesforce EventLog Cloud Collector
- SentinelOne Alerts Cloud Collector
- SentinelOne Cloud Funnel Cloud Collector
- SentinelOne Threats Cloud Collector
- SentinelOne Cloud Collector
- ServiceNow Cloud Collector
- Slack Cloud Collector
- Snowflake Cloud Collector
- Sophos Central Cloud Collector
- Splunk Cloud Collector
- STIX/TAXII Cloud Collector
- Symantec Endpoint Security Cloud Collector
- Tenable Cloud Collector
- Trend Vision One Cloud Collector
- Trellix Endpoint Security Cloud Collector
- Vectra Cloud Collector
- Zoom Cloud Collector
- Zscaler ZIA Cloud Collector
- Webhook Cloud Collectors
- Wiz Issues Cloud Collector
- Wiz API Cloud Collector
- Troubleshooting Cloud Collectors
Prerequisites to Configure Azure Blob Storage Logs Cloud Collector
Before you configure the Azure Blob Storage Cloud Collector you must complete the following prerequisites.
Configure Azure Storage account – Configure a queue and endpoint details, set permissions for the SAS token, and obtain storage account properties.
Obtain tenant ID, client ID, and client secret.
Assign the required roles to the Azure Storage account.
Configure Azure Storage Account
The Azure Storage Cloud Collector consumes data stored in Azure Storage Accounts to retrieve various Azure data sources.
An Azure data source stores data in:
Azure Storage Account's Blob store – The store must be StorageV2 to alert its queue on new blobs.
Clear-text files with one event per line. For example, .log or.txt format. You can also use JSON-line format with each line as a valid event in JSON format.
Use the following steps to configure a queue and endpoint details, set permissions for the SAS token, and obtain storage account properties.
Go to the the storage account where that data that you want to consume is located.
Go to https://portal.azure.com.
Navigate to Storage Accounts and then select your storage account.
Verify the type of storage is StorageV2 in the storage accounts table, or in the Overview > Account Kind.
Configure a Queue in that storage account to be notified when new Blobs are added to its blob store.
Create a queue dedicated for the connector.
Navigate to Queues.
Click + Queue, name it something unique, for example
sk4queue, and then click OK.Record the queue name for later use.
Navigate to Events.
Click + Event Subscription.
Enter a descriptive name like
notify-sk4queue-on-new-blobs.Verify that Events Schema are set to the default Event Grid Schema.
Under Event Types > Filter to Event Types make sure only the Blob Created is selected.
Configure the Endpoint Details:
In Endpoint Type, select Storage Queues.
In Endpoint, click Select an endpoint.
In the panel that opened, select the subscription where the current Storage Account is located.
Select the storage account.
Select the queue that you created in the first step, for example
sk4queue.Confirm Selection.
Click Create.
While the queue and the blob can be created in different storage accounts, for the sake of simplicity, they're configured in the same storage account.
Create minimal-permissions SAS tokens.
Navigate to Security + Networking > Shared access signature.
Create a SAS token for the blob storage.
Select the Blob from the Allowed services section.
Select the Object from the Allowed resource types.
Select the Read from the Allowed permissions.
Set the End time to a time far in the future, for example 10 years in the future, so the connector doesn't stop working because of SAS Token invalidation.
Click Generate SAS and connection string.
Copy the value from the SAS Token field.
For example, the token can look like
?sv=2018-03-28&ss=q&srt=o&sp=p&se=2019-09-23T17:52:57Z&st=2019-09-23T09:52:57Z&spr=https&sig=aASkYB8%2BGf21fMXl3Bnf0Mod7n81Dq8E%2FeggjEQr%2BD8%3D.
Note
Similarly, create a SAS Token for Queue with the following settings.
Allowed services: Queue
Allowed services resource types: Object
Allowed permissions: Update and Process
Obtain other Storage Account properties.
Navigate to Properties.
Record the value from the Primary Queue Service Endpoint field, under the Queue service section.
Proceed to Configure the Azure Storage Logs Cloud Collector.
While configuring the cloud collector, select Azure Storage - SAS Tokens as the authentication method and configure the Sync Strategy.
Obtain Tenant ID, Client ID, and Client Secret
To obtain the Tenant ID, Client ID, and Client Secret, create a Microsoft Entra ID application (formerly called Azure Active Directory) in the Microsoft Azure portal using the following steps.
Create and Register a Microsoft Entra ID Application
Log into your Azure account by accessing the Azure portal.
From the available Azure Services, select Microsoft Entra ID (formerly called Azure Active Directory).
From the left navigation pane, select App Registrations, then click New Registration.
On the Register an application page, enter the following information:
Name – Specify a name for the new application. For example, Exabeam MS Entra ID App.
Supported account types – Select the account type Accounts in this organizational directory only.
Redirect URI – (Optional) Select the Web platform and specify a URI.
Click Register. When registration is complete, the Overview tab of the new application is displayed.
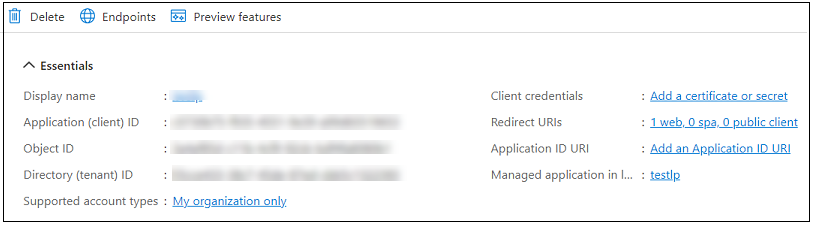
Copy and make a note of the values for both the Application (client) ID and the Directory (tenant) ID. You will need these values when configuring a Microsoft cloud collector.
In your new Microsoft Entra ID application, click Certificates & secrets in the left navigation pane.
On the Client Secrets tab, click New client secret.
Enter a description and an expiration period for the secret.
Click Add.
Copy and make a note of the value of the new client secret that the Client secrets tab displays.
Assign the Required Roles to the Azure Storage Account
To assign the Storage Blob Data Contributor and the Storage Queue Data Contributor role to the Azure storage account, use the following steps:
On the Azure portal, navigate to Storage Accounts and select your storage account.
In the left pane, click Access control (IAM).
Click Add and then click Add role-assignment.
In the Add role assignment section, under Role, search for and select Storage Blob Data Contributor, and Storage Queue Data Contributor roles.
Click Next.
In the Members section, click Select Members.
Search for and select your Microsoft Entra ID application.
Click Next and then click Review + assign.
After the role is assigned to your storage account, the storage account has permission to read, write, and delete blob data in Azure Storage containers and read and write messages to Azure Storage queues.
